It looks like I'm headed to IT Sec World this year. This is a convention with seminars for Health, financial and government IT workers.
The seminars appear to be a re-hash of things I'm always familiar with, but I figure I'll be using this as a network opportunity as well as a way to get my finger back on the pulse of financial services InfoSec.
Does anyone else plan on attending?
2008-04-29
IT Security World 2008
Labels: conventions, HiR Info, meetings
2008-04-28
What a crazy weekend!
Saturday, I set up my Jornada 720 with the enGenius 200mW card, a Garmin GPS12 (olde school) and a pair of 19dBi antennae. I used Kismet running on JLime Linux. About 3:00 PM, I hit the road with my wife. Here's the setup in the car.
Only in rural Missouri... What the hell?
And if that's not strange enough, I hit a low-flying goose (yes, a big, huge Canada Goose) about 10 miles outside of town. I had to limp my car into town. I could see, but only just. And speeds higher than 50 MPH or so made the windshield cave in more. Yikes!

After we got into town, it was off to 1984. 1984 is an arcade that looks quite literally like it got put in a time machine and beamed here.
They even have a Mac Classic running all of their business software!
Darren tries his hand at BattleZone (a cheesy tank battle sim)
Darren and Sl4cker
Gauntlet!
After we got tired of the arcade, we grabbed some sandwiches, then took off to a bar for beer, gadgets, pool, and more beer. And some pool. And shots. Then more beer. And after I left, I think they had more beer too.


This is Adam, the new owner of Jordan Valley Pedicabs. He manages 5 pedicabs in the area, and who knows how many "drivers" around in Springfield. You haven't really lived until you've tried riding in the back of a three-wheeled bicycle while rather inebriated.
More carnage. My wife and I were stranded in Springfield since there were no glass repair shops open on Sunday.
We spent some time with family friends north of Springfield while we were waiting for my windshield to get fixed up. They have cows in their back yard. This is definitely Missouri.
Life's no fun unless you're geeking out and wrenching on stuff at least once a day. I helped Ray install an electronic cruise control system on his Vulcan 2000. Wiring diagrams, Fluke testers, soldering iron, and lots of shrink tubing made up most of my Sunday.
I didn't get many good pictures of the Hak5 meetup because it was too dark and I didn't have a tripod (and my camera is crappy). I think Darren and Snubs will likely have a bunch of photos up sooner or later. We'll have to see.
My Kismet/JLime/200mW/19dBi Dipole rig found about 6,500 networks this weekend. About half of those were new, never reported to WiGLE. Another weekend like this will boost me to WiGLE's top 100.
Edit: If photos aren't working, try this album link.
2008-04-25
Weekend Blurbs
Sorry I haven't finished up my series on Web Filter Evasion yet. I had most of the articles pre-written except this last one and life's been kind of busy this week. I don't even know if I'll get around to Sysadmin Sunday the way this weekend looks.
Speaking of which, we could use more writers for security, electronics, or other geeky topics. You don't need to be in the KC area, but it would help. Feel free to drop us a line in the comments.
Tonight's The Friday Geek-Out at Daily Dose in Overland Park, KS. I'll probably be there around 11:00PM.
Darren published meetup details so maybe we'll see you there. If you're around KC and want to convoy or car pool, let us know in the comments. We'll probably roll out from KC around 3:00 tomorrow (Saturday) afternoon.
Pics will follow, I'm sure.
2008-04-21
Who's down for a trip to Springfield, MO this weekend?
Midwest-region hackers.
Darren from Hak5 will be kicking it in Springfield, MO this weekend (April 24-29th, actually) and I'm planning on heading down there to hang out, get a few drinks, and what have you. Drop a comment and I'll try to get more info to you.
Labels: blogs, computer hacker, meetings
Web filter evasion part 4: Public HTTP Proxies
View entire series: Web Filter Evasion
A lot of times, you kind of want access to your favorite content, even if it's just to read it, while at work or school. Some places with more draconian Internet access policies block pretty much everything "cool" and paint their restrictions with a very wide brush. In this series, we'll uncover a few ways around these restrictions.
With each article, I will delve into techniques that are progressively more advanced and difficult to implement. Keep in mind that this is a thought exercise in evasion. Implementing this stuff could get you expelled from school, fired from your job, or banned from public-access computers in a library or coffee shop. With a little bit of wisdom, you can often get around the restrictions set in place without getting yourself into hot water.
Today, we will cover using "wide open" proxies to bounce our connections through. Since proxies are transient and often configured poorly, they pass the ire of most web filters. The rub? You usually have to find one that operates on a well-known port such as 80 (http) or 443 (https/ssl). Finding a working proxy can be a pain, and using it involves tweaking your browser settings and/or installing special software. Group policies could leave you in the cold on this one. The increased difficulty of this particular evasion technique brings this trick in at #4 in our series.
Public Proxies
Public proxies are (often SOCKS v5) proxy servers that have either been intentionally or accidentally configured to allow anyone on the Internet to access proxied content without proper access controls. I could go on and on about the various security implications of these proxies but that's not what this series is about. Simply put, HTTP proxies differ from Web Proxies in that the browser directly handles communication with the proxy behind the scenes. Regardless of what protocols the proxies are capable of handling, we're only concerned about Web traffic (http/https) for the time being.
Browser Configuration:
Yesterday, I linked to various proxy configuration instructions for different browsers. Today, you can use the same instructions to add the proxies you discover on your own. If you find that there is already a proxy server configured, you might be out of luck for this trick (and maybe for the fifth and final one, as well). If your employer is already forcing your web traffic through their own proxy, there's a good chance that they're blocking all outgoing traffic from your workstation to the Internet, making HTTP Proxies AND Tunneling difficult, if not impossible.
Security Risks:
The same risks apply here as apply to web proxies. Your data is going through a third party and you're subject to data manipulation, sniffing, or other bad things. Essentially, you're trusting a potentially unknown and untrusted third party with your traffic. By now, it should be obvious that these more aggressive evasion techniques can't be easily justified. You have been warned.
Finding public HTTP Proxies:
Public proxies play a huge role in the so-called underground. I'm talking mostly about illegal or frowned-upon activities such as phishing, spamming, and illegal file sharing. As such, there are groups that go out of their way to sniff out and enumerate poorly-configured proxy servers that are easily hijacked for whatever purpose others desire. I don't advocate using services without permission. In a moment, I'll discuss how to set up your own public HTTP Proxy.
One source that provides a list of proxies that can be sorted on several criteria: http://www.xroxy.com/proxy-port.htm
Assuming your employer or school has you locked down to using only port 80 or 443, use the above tool to find proxies that operate on those ports. Then, update your proxy settings to match one of the servers in the list. If it's too slow or fails to work, try again. Soon enough, you should be able to access all of the content your heart desires.
Squid at home (or on another server outside of work/school)
You can also configure Squid to act as your own proxy. Making it a public proxy is a bad idea, so lock it down to your remote computer's IP Address. First, find your public-facing IP address from the computer you normally use, and write it down. The easiest way is to visit WhatIsMyIP.com. Then, using the Squid configuration guide from yesterday, add the following lines:
At the top of the block of "acl" lines (replace with your actual ip address in place of 65.43.2.1):
acl myremote src 65.43.2.1 255.255.255.255
Above the other http_access lines:
http_access allow myremote all
Finally, you will need Squid to listen on a port you can use. For this example, we will use Port 80. Keep in mind this will interfere with any web server running on this host. Below the existing http_port line(s), add:
http_port 80
Restart Squid, then point your browser's proxy to the IP address of your squid server, port 80.
The IP Address restriction of "myremote" will keep others from hijacking your proxy. Add as many rules as you need to for other remote IP addresses.
View entire series: Web Filter Evasion
Labels: evasion, hack, InfoSec, proxy, web filter
2008-04-20
Sysadmin Sunday: Squid Cache
What is Squid?
Aside from something Bruce Schneier writes about every Friday, "Squid is a caching proxy for the Web supporting HTTP, HTTPS, FTP, and more. It reduces bandwidth and improves response times by caching and reusing frequently-requested web pages. Squid has extensive access controls and makes a great server accelerator. It runs on Unix and Windows and is licensed under the GNU GPL." -- taken from Squid-Cache.org, as I couldn't explain it any better myself.
On your network, you can set up Squid on a reasonably well-endowed server for the purposes of manipulating certain Internet traffic - specifically HTTP, usually for the purpose of increasing load times on frequently-visited content. There are other things you can do with Squid, such as blocking advertisements or turning all of the images upside down (or is that umop ap!sdn). For now, though, we'll set up a Squid server in our lab on our AMP (Apache/MySQL/PHP) fun box, running Gutsy server.
Getting and Installing Squid
Many operating systems' package installers have Squid available for installation. Squid has a list of binary packages for popular operating systems, but building Squid from source code is trivial at best (with a ./configure && make && sudo make install ) but for the sake of cleanliness, I'll just do a sudo apt-get install squid on Ubuntu.
Making Squid Work
Squid must have a cache directory that it can store the data in. If the package installation did not create this, then you must run (as root), squid -z, which will create the cache directory. You should also make sure that squid will start by default. If you reboot and squid isn't running, adding "squid" to your rc.local file is the easiest way, but there could be a start-up script somewhere that would do a more elegant job.
Proxy settings on your workstation(s)
Squid, by default, runs on port 3128. To enable proxy for your workstation, you will need to know the IP Address of your Squid server, and when asked for what port the proxy runs on, enter 3128. Here are some links for setting up Proxy in various browsers. Just remember to use your Squid IP and Port in place of any example proxy configuration used.
Now what?
At this point, you likely have a Squid server up and running with the basic default configuration enabled, and for the most part, it's completely useless. Shown below, I've pointed Safari's proxy settings to the Squid server then attempted to access HiR Information Report to no avail.

To fix this, find the ACL lines in squid.conf (on Gutsy, it's /etc/squid/squid.conf) and simply add a line define your local network. Obviously, you would want to replace this with your own IP subnetting information.
acl localnet src 192.168.0.0/255.255.255.0
Then, find the http_access lines and add a line (preferably above all of the other http_access lines) allowing machines on the local network to get out to the rest of the Internet:
http_access allow localnet all
After re-starting squid (killall squid, pkill squid, /etc/init.d/squid restart, etc...) I can access anything through squid, and the pages will now be cached. This will reduce the bandwidth used for day-to-day web browsing and make pages seem to load faster. For a small business running on typical consumer broadband connections, this is a quick and easy way to increase browsing performance. Also, operating system patches will only be downloaded once and then cached. When the time comes to do the updates on all of the workstations, this trick will make life a little easier for you.
If you wish to force all HTTP traffic through Squid (for instance, if you yourself are planning on implementing a Web filter with Squid) and you have a somewhat flexible router or firewall, you can block all outgoing traffic destined for port 80 and 443 except for traffic coming from the Squid server. That, however, is beyond the scope of this article.
Tomorrow, you'll learn how to tweak a few options for Squid so that you can use it to evade web filters in the fourth article in my ongoing web filter evasion series.
2008-04-19
Web filter evasion part 3: Anonymous Web Proxy
View entire series: Web Filter Evasion
A lot of times, you kind of want access to your favorite content, even if it's just to read it, while at work or school. Some places with more draconian Internet access policies block pretty much everything "cool" and paint their restrictions with a very wide brush. In this series, we'll uncover a few ways around these restrictions.
With each article, I will delve into techniques that are progressively more advanced and difficult to implement. Keep in mind that this is a thought exercise in evasion. Implementing this stuff could get you expelled from school, fired from your job, or banned from public-access computers in a library or coffee shop. With a little bit of wisdom, you can often get around the restrictions set in place without getting yourself into hot water.
In Part 3, I am going to discuss using web "privacy" or "anonymizer" proxies. It's number three on the list because it is simple to use and often free -- risks be damned. These often free (but occasionally subscription-based) web sites provide you with a special URL that you visit, whereupon you enter the URL you wish to visit. These sites often claim to keep rogue websites from storing cookies or executing scripts on your computer, while others focus on evading web filters or blocking ads.
Risk of getting punished if caught
Regardless, you will have a difficult time weaseling your way out of this stunt if you're caught. The only reason you'd want to use proxies such as these one while in a web-restricted environment is to evade the restrictions. There's no innocent sweet-talking that will save you here. Also, many web filtering companies specifically play cat-and-mouse with these kinds of services, often blocking them shortly after they appear. Users who trigger this rule on a web filter are almost certainly going to get a visit from a higher-up.
Security risk of using proxies
Any time you use a proxy, you are routing traffic through someone else's network. While it's true that all Internet traffic hits various networks, the operators of proxies KNOW that people are using their services either for privacy or filter evasion. As such, not all proxy providers are guaranteed to be trustworthy, including those listed below.
Managed Web Proxies Megaproxy offers a free trial. It was one of the first web-based anonymous proxies, with the intended purpose of keeping cookies and ads at bay, making it more difficult for site owners to gather data about you. The (perhaps unintentional) side effect was that people who could access the it from behind a web filter service could often use it to access blocked content. The paid version has a much more obscure and innocuous URL that isn't likely to make netadmins question it, but its URLs are most likely blocked on commercial filtering software because they go to great lengths to find most of the high-profile ways to evade. I actually did subscribe to this service many years ago, but I've since let it lapse. I was generally happy with it while I used it.
Megaproxy offers a free trial. It was one of the first web-based anonymous proxies, with the intended purpose of keeping cookies and ads at bay, making it more difficult for site owners to gather data about you. The (perhaps unintentional) side effect was that people who could access the it from behind a web filter service could often use it to access blocked content. The paid version has a much more obscure and innocuous URL that isn't likely to make netadmins question it, but its URLs are most likely blocked on commercial filtering software because they go to great lengths to find most of the high-profile ways to evade. I actually did subscribe to this service many years ago, but I've since let it lapse. I was generally happy with it while I used it. Privax offers an extensive list of (what appear to be free) Anonymous Web Proxies. The catch being here that there are many different URLs you can visit, with the hopes one or more won't be filtered. Some addresses blatantly announce that it's a proxy service while others are less obvious. Like other web proxies, Privax places a secondary navigation bar at the top of every page, making it easy to tell if the stuff you're looking at is, in fact, being proxied. I haven't extensively used Privax before, but it looks like a decent solution as I sit here now and try some sites through it.
Privax offers an extensive list of (what appear to be free) Anonymous Web Proxies. The catch being here that there are many different URLs you can visit, with the hopes one or more won't be filtered. Some addresses blatantly announce that it's a proxy service while others are less obvious. Like other web proxies, Privax places a secondary navigation bar at the top of every page, making it easy to tell if the stuff you're looking at is, in fact, being proxied. I haven't extensively used Privax before, but it looks like a decent solution as I sit here now and try some sites through it.
Set up your own For a while, I ran my own CGI Proxy on a hosted server that I could access from anywhere. If you have web space, this is a way to set up your own proxy under the radar, especially if you access it via SSL. The down-side is that many web-based anonymizers that you can host yourself (there are others, written in PHP, Perl, etc) lack some of the more advanced functionality of the commercial "anonymizer" providers. If setting one up yourself, be sure to use a method of password protecting your proxy so that it can't be abused by others who stumble across it.
For a while, I ran my own CGI Proxy on a hosted server that I could access from anywhere. If you have web space, this is a way to set up your own proxy under the radar, especially if you access it via SSL. The down-side is that many web-based anonymizers that you can host yourself (there are others, written in PHP, Perl, etc) lack some of the more advanced functionality of the commercial "anonymizer" providers. If setting one up yourself, be sure to use a method of password protecting your proxy so that it can't be abused by others who stumble across it.
Tomorrow on Sysadmin Sunday, I'll discuss setting up Squid, a caching HTTP proxy. This is different than a Web or CGI proxy, but it can be used to evade web filters as well. On Monday, I'll pick up the series again and discuss how to bypass web filters with your new Squid server.
Read the whole series: Web Filter Evasion
Labels: evasion, hack, InfoSec, proxy, web filter
2008-04-18
Evil Mad Scientist Sawed-Off USB Drive
A nifty hardware mod just came though my RSS reader: the Sawed-Off USB Key. I find the novelty of the mod funny, but the idea in general is quite nice. Finding interesting places to put a stripped USB key is a fun and/or useful way to carry your data. Stuff like the wooden USB sticks (DIY), Hot Wheels Mini Cooper mod, and several others linked on a Squidoo page give some of the range people have done. Most are simply cosmetic mods that stick a drive in something, others are more artistic and hide the drive itself unless in use. Post a comment with any other good ideas for hiding your thumb drive from prying eyes.
Novelty Flash Drives ( working bike lock flash drive!)
More links via Daily Cup of Tech.
Laptop Key USB drive mod
2008-04-17
Web filter evasion part 2: Out of band
 View entire series: Web Filter Evasion
View entire series: Web Filter Evasion
A lot of times, you kind of want access to your favorite content, even if it's just to read it, while at work or school. Some places with more draconian Internet access policies block pretty much everything "cool" and paint their restrictions with a very wide brush. In this series, we'll uncover a few ways around these restrictions.
With each article, I will delve into techniques that are progressively more advanced and difficult to implement. Keep in mind that this is a thought exercise in evasion. Implementing this stuff could get you expelled from school, fired from your job, or banned from public-access computers in a library or coffee shop. With a little bit of wisdom, you can often get around the restrictions set in place without getting yourself into hot water.
In Part 2, I'll cover out-of-band communication. Why spend time trying to trick the web filter when you can simply not go through it at all? Creeping into our list at number two, this trick is somewhat obvious and well-documented. Most computer users can manage to connect to a wireless network or follow the instructions that come with a mobile data service plan.
Personally, this is what I do most of the time. I'm using my own laptop and my own internet connection. Where I work, I'm not breaking any rules at all, so long as the content I'm browsing doesn't offend my peers. If I'm not disturbing anyone and I'm getting my work done, my boss doesn't mind.
Problems
- Cost. To properly implement something like this, you'll likely need a laptop computer, Wi-Fi enabled PDA, a smartphone of some sort, or other expensive equipment.
- Totally uncontrolled access. Neither IT Departments nor managers are often comfortable when you have 100% unfettered access to whatever you want. This could get you in trouble.
- The fact that you'll be avoiding connecting through the work or school network means that anything on your computer is NOT on the work or school network. This is sometimes a sigh of relief for netadmins.
- What you do out-of-band can't be monitored by the network, either.
Wi-Fi
If you feel like getting a little bit more advanced in your search for a public network to piggyback, install wireless scanning software (KisMAC, BSD Airtools, Kismet or Netstumbler), pick up some high-gain antennae and a high-power wireless ethernet card. The widespread deployment of privately-operated, free Wi-Fi makes this a viable option in dense urban and business districts.
Mobile Data plans (Wireless broadband)
Also in the same vein are smartphones. Gadgets such as the iPhone offer feature-packed browsing via the phone's data plan. You can also get on AIM/MSN/Yahoo or check many websites and mail providers through the built-in WAP Browser on less advanced mobile phones.
Mobile Phone Tethering
This is a little more shady, and could get your account terminated with your wireless carrier. By plugging in a cable between your laptop and mobile phone (or using bluetooth to make the connection) you can "tether" and use your phone's built-in data connection to access the Internet. HowardForums is a good place to learn about this stuff in more detail.
Next in this series, we'll dive head-first into web-based anonymous proxies -- a sure-fire way to get your IT guys angry at you, should you be caught in the act.
View entire series: Web Filter Evasion
2008-04-15
Web filter evasion part 1: RSS and You
View entire series: Web Filter Evasion
A lot of times, you kind of want access to your favorite content, even if it's just to read it, while at work or school. Some places with more draconian Internet access policies block pretty much everything "cool" and paint their restrictions with a very wide brush. In this series, we'll uncover a few ways around these restrictions.
In Part 1, I am going to cover one way of evading these restrictions that is not only one of the most straightforward and easy methods, but also the least likely to get you in trouble with your boss or your IT department: Online RSS readers.
About RSS
RSS was invented around the turn of the century, but started to gain widespread popularity in the wake of so-called "Web 2.0", when syndication, mash-ups, cross-platform publication and content management all coalesced together. While not every web site has an RSS feed, almost every blog, news site and social network has some kind of RSS integration going on. In this article, I'll focus on gaining access to content via RSS despite web filtering software's strangle-hold.
Local RSS Clients
Local RSS clients such as FeedReader or Mozilla Firefox Live Bookmarks usually contact the site directly, pulling a data feed down (RSS, Atom, XML, etc) to display the information in a lightweight, easy-to-read format. The problem with this is that the RSS feed usually has the blocked URL in it. For example, Digg's rss feeds are all on digg.com. If access to Digg is blocked, you can't get to the feeds, either.
Online Readers
Online RSS readers pull the feed from a central server, then just display the information to you directly over the web. For this example, I'll use Google Reader. That said, My Yahoo and MSN Live (among dozens of others) also offer the ability to integrate feeds on your page but it's not quite as robust as Google Reader. Using the example above, if you add Digg's RSS feeds to Google Reader, your web filter only sees you trying to access http://www.google.com/reader/ which is passing the contents of the RSS feeds to you - and most web filters let you get to Google. Again, if that doesn't work, there are dozens of ways to access RSS feeds with online readers.
Things to note
One flaw here is that embedded content from banned sites won't load and may be logged in your web filtering software. If your employer blocks Flickr, you can load someone's Flickr RSS feed into your reader and see their feed, but all of their images will fail to load. Same goes for blog posts with embedded YouTube videos if YouTube is blocked. You get the idea. Basically, this works best for RSS feeds where most of the content is text-based. News sites like CNN or Engadget. Social bookmarking sites like Digg, delicious and reddit. Blogspot, wordpress or livejournal blogs. Even twitter.
Justification
If you get busted (which is not likely if you play your cards right), you can always say that you use something like Google Reader to track updates to your favorite websites at home. If you can get to it from work, it must be okay, right? Make sure you're managing your time wisely, and keep the content you view at work "work safe" and non-offensive. Chances are that your boss won't mind. In fact, he might just think you're checking your personal email really quick, as RSS readers often look somewhat similar to web mail clients. Plausible deniability only works once, though. If you're asked to stop it, you should stop. If your written policy specifically bans all personal Internet browsing, you may also get the book thrown at you. HiR won't be held responsible for legal or employment problems.
How to do it:
First, sign up for a free Google account if you don't have one already.
Next, go to Google Reader and log in.
Add a subscription RSS feed. I'll add HiR Information Report to my Google Reader:

In part 2, I'll cover using out-of-band communication.
View entire series: Web Filter Evasion
2008-04-11
JLime Linux - WiFi Scanning, New Userland, etc...
Almost all of the problems I was initially having with jlime were due to the fact that when I downloaded it, they were in the middle of a big update with an experimental kernel and an old base userland image. After pulling down the new userland and going to a known-stable kernel, everything seems to be rockin' and rollin' with jLime on my Hewlett Packard Jornada 720.
Case and point, X now has a decent interface, desktop icons, and Torsmo status monitor works great (finally!)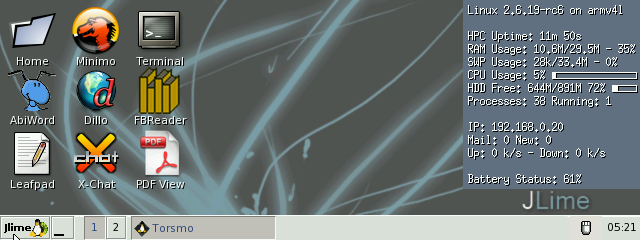
I was also having problems with package management. Those were also resolved by installing fresh from the current userland image. The packages are also pretty up-to-date with a quite extensive list of things to choose from. Want nmap? MySQL? OpenSSH? No problem! Kismet for War-driving? Just say the word! Here's my J720 running Kismet with a Senao Engenius 200mW Long-range 802.11b card attached to a pair of 19dBi omni-directional magnet mount antennae.
And a close-up of the screen: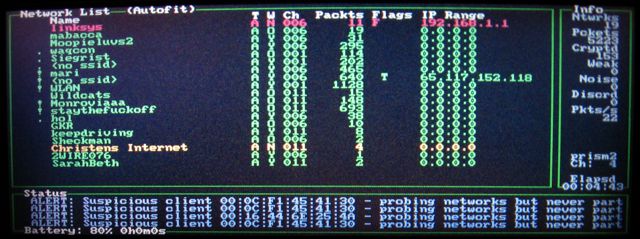
All this, and my battery lasts for hours upon hours, even with the wireless card installed. I actually have nothing left to complain about at all aside from the fact that 32MB of RAM and 206 MHz is still a somewhat anemic machine for web browsing. For light-weight stuff like checking e-mail, managing servers via SSH and the like, this seems to be just about the most handy thing I've seen in a very long time.
I'm working on getting a data cable for my new GPS so that I can really put this thing to the test when it comes to war-driving. I haven't ever used kismet for serious network location. I'm more of a Mac OS X and BSD guy at heart, so KisMAC and BSD-Airtools are my typical weapons of choice.
It's simply amazing to me, though, to see this kind of development happening for a family of portable computers that's been more or less dead for the better part of a decade. Where I was once drooling over the OLPC and EEePC, I'm now finding that I have all of the ultra-mobile goodness I really need right here in a package that's admittedly slower but also lighter, smaller and longer lasting.
Labels: handhelds, jornada, linux, Operatingsystems, wireless
ApacheFriends XAMPP makes Apache setup easy
 I've been using XAMPP on Windows (which I'm forced to use at work) for a few years. I write a lot of custom PHP stuff to help me with my day job, and I also like to test functions or classes I write before I push it out to production. ApacheFriends XAMPP is an easy way to get a basic Apache installation up and running with some of the most popular add-ons including PHP and MySQL. It installs in OS X and many Linux distributions as well.
I've been using XAMPP on Windows (which I'm forced to use at work) for a few years. I write a lot of custom PHP stuff to help me with my day job, and I also like to test functions or classes I write before I push it out to production. ApacheFriends XAMPP is an easy way to get a basic Apache installation up and running with some of the most popular add-ons including PHP and MySQL. It installs in OS X and many Linux distributions as well.
While nothing can replace a streamlined, custom-compiled AMP Stack set up just the way you need it, XAMPP affords busy sysadmins (and web developers that don't want to be sysadmins!) the ability to get a functional web dev environment up and running with ease.
Go ahead, give XAMPP a shot!
2008-04-10
KC BSD User Group - April 2008
We switched locations this month to the downtown Central Library at 10th and Wyandotte. The meeting rooms are a lot nicer. Remember, the meetings are the second Wednesday of each month.
We discussed a smorgasbord of topics, most of which at least somehow related to BSD in one way or another. This included (but was not limited to):
- SSH Tunneling
- Proxy configuration
- VPN using BSD-built in and third-party software
- Network layout and BSD router configuration
- Programming in various interpreted scripting languages
- Electronics and embedded computing
Labels: bsd, kansascity, meetings, unix
2008-04-09
Shell script for Flickr/Blogger Goodness
Embed your Flickr images into blogger while linking to their page (as opposed to just the image itself). Like this (not my image, just an interesting one I found):
Just edit the flickrbase url in the script, and enjoy. Run the script with the image URL in the command-line, and it gives you the HTML to paste into blogger.
Note, this won't link to other peoples' flickr pages as-is, nor can it tell you the username for any given flickr image. If you want to embed someone else's flickr images, you'll need to edit the flickrbase url to match that of the person whose images you wish to use. Although I don't advise shameless ripping of other peoples' stuff.
Script is available here:
http://stuff.h-i-r.net/blogstuff/fr.sh
2008-04-07
"Hacking" MediaWiki PasswordProtected extension
I say "Hacking" because this is so retarded that I can't even believe it.
A group I'm working with (not directly related to HiR Information Report) is thinking of setting up a Wiki on the network for internal collaboration as well as communication of policies and contact information to other groups within the organization. They want some stuff (for instance, step-by-step audit documentation) to be shielded from view. This isn't Internet-facing, but it's stuff that no one else really needs to know. With that, they had the sysadmins install MediaWiki installed with the PasswordProtected extension.
Usage is simple. You use a "password" tag object around the text of the password you want to use.
Bypassing it is even simpler. Just look at the page history of the password protected page. There, in plain text, lies the password for all to see. See, I told you I couldn't justify saying "hacking" without putting quotes around it. I've been unable to get in touch with the maintainer of this extension.
Consider me disgusted. If you use this extension, quit fooling yourself. I guess it's back to the drawing board for my friends, though.
2008-04-06
Sysadmin Sunday: Linux and BSD Filesystem attributes
Most sysadmins are familiar with the concept of file ownership and permissions. Read, Write, and Execute are ingrained in our memories from the start. Sometimes, though, that's not enough. Here are some extended attributes for files in Linux and *BSD:
BSD:
To set file flags in BSD, use chflags. To view them, use ls -lO. Flags are as follows (from the chflags(1) man page):
schg and sappnd are particularly useful. As described, they place files in an append-only or immutable state, where nothing, not even root can break the rules without first going into single-user mode and disabling the flag. uchg will keep you from accidentally clobbering an important file as well, but can still be un-set by you.
arch, archived
set the archived flag (super-user only)
opaque set the opaque flag (owner or super-user only). [Directory
is opaque when viewed through a union mount]
nodump set the nodump flag (owner or super-user only)
sappnd, sappend
set the system append-only flag (super-user only)
schg, schange, simmutable
set the system immutable flag (super-user only)
uappnd, uappend
set the user append-only flag (owner or super-user only)
uchg, uchange, uimmutable
set the user immutable flag (owner or super-user only)
hidden set the hidden flag [Hide item from GUI]
As discussed in chflags(2), the sappnd and schg flags may only be unset
when the system is in single-user mode.
Putting the letters ``no'' before or removing the letters ``no'' from a
keyword causes the flag to be cleared. For example:
nouchg clear the user immutable flag (owner or super-user only)
dump clear the nodump flag (owner or super-user only)
Example viewing, setting, and demonstrating the uchg flag:
Chimera:Documents axon$ ls -lO
total 32
-rw-r--r-- 1 axon staff - 8258 Apr 6 19:16 description.html
-rw-r--r-- 1 axon staff - 21 Apr 2 12:25 file.doc
Chimera:Documents axon$ chflags uchg description.html
Chimera:Documents axon$ ls -lO
total 32
-rw-r--r-- 1 axon staff uchg 8258 Apr 6 19:16 description.html
-rw-r--r-- 1 axon staff - 21 Apr 2 12:25 file.doc
Chimera:Documents axon$ rm description.html
override rw-r--r-- axon/staff uchg for description.html? y
rm: description.html: Operation not permitted
Chimera:Documents axon$ chflags nouchg description.html
Chimera:Documents axon$ rm description.html
Chimera:Documents axon$ ls -lO
total 8
-rw-r--r-- 1 axon staff - 21 Apr 2 12:25 file.doc
Linux:
Use chattr to set attributes and lsattr to view them.
From the chattr(1) man page:
The format of a symbolic mode is +-=[ASacDdIijsTtu].
The operator ‘+’ causes the selected attributes to be added to the
existing attributes of the files; ‘-’ causes them to be removed; and
‘=’ causes them to be the only attributes that the files have.
The letters ‘acdijsuADST’ select the new attributes for the files:
append only (a), compressed (c), no dump (d), immutable (i), data jour‐
nalling (j), secure deletion (s), no tail-merging (t), undeletable (u),
no atime updates (A), synchronous directory updates (D), synchronous
updates (S), and top of directory hierarchy (T).
As you can see, most of these attributes are similar to the BSD flags. We'll do the same thing on Linux with the immutable attribute.
axon@hosting:~/hir-test$ lsattr
------------------ ./internet-resume.doc
------------------ ./mail.sql
axon@hosting:~/hir-test$ chattr +i mail.sql
axon@hosting:~/hir-test$ lsattr
------------------ ./internet-resume.doc
----i------------- ./mail.sql
axon@hosting:~/hir-test$ rm mail.sql
rm: remove write-protected regular file `mail.sql'? y
rm: cannot remove `mail.sql': Operation not permitted
Trying this... Posting from jlime
Thanks to a tip from a jlime forum denizen, I found out that an older kernel would work better on my Jornada 720. Suspend works, WiFi works, even the Torsmo status app works better. Minimo didn't like Blogger, but the Dillo browser seems to be working albeit in a really minimalistic way like you'd expect in a phone's browser.
In short, this is actually a completely functional networked Linux PDA right now. I'll keep this around and do some periodic reviews as I further use this platform.
Labels: handhelds, jornada, linux, Operatingsystems, unix
2008-04-05
UNIX variants on HP Jornada Palmtops
We covered this a bit at the 2600 meeting last night. I don't have a lot of time to go into detail, but here's a quick breakdown.
Asmodian X got me hooked on Windows CE Palmtops back in late 1997. I picked up a floor model HP 300LX for cheap, and actually used it as my main computer (including Dialup BBS, Telnet, Mail, and web browsing) for quite a while. It was more than sufficient for typing my papers for class and interfacing with the UNIX servers. Asmo also had a Casio Cassiopeia running CE, so we tinkered with this stuff a LOT back in the day.
Later, at DefCon 6, we'd run into a guy with an HP 620LX. That thing had a full color screen and a significant boost in memory, not to mention sound recording ability. This all sounds cheesy now, but it blew away the devices we had with their four or 16-color greyscale screens.
As time has progressed, I've also acquired an HP 320LX (same as 300LX but with a backlit screen and more RAM), a Jornada 680e (Refurbished Dutch Railways model) and a Jornada 720.
The HP300's are currently packed away somewhere, but the Jornadas are alive and well.
I was considering NetBSD and Linux for this project, but I found out that the NetBSD project for these pretty much died once they could say "it boots!" You have to use a serial cable for the console. In other words, it's useless until someone ports wscons and some device drivers. So, I chose JLime Linux, which is still in active development -- the kernel build on my 720 (Mongo branch) is less than two weeks old!
To install JLime, you need a CF card that's at least 128MB. You create 3 partitions:
- FAT partition usable from within Windows CE
- ext2 partition for Linux to run from
- Swap partition for virtual memory
Once you insert the card into the PDA and run the boot loader, all of the PDA's memory will be completely wiped, so all files and data on it will be lost. Windows CE stays in ROM so when you reboot, Windows CE will be back in initial setup mode.
I actually put the boot loaders and zimages for both the J680e and the J720 on the FAT partition, created two different ext2 partitions, and left one shared swap partition on my 2GB CF card. Had I been thinking, I would have made a third ext2 for a shared home directory between the two PDAs.
Right now, here's the status of them:
Jornada 680 running jLime (Donkey):
- Boots Linux, loads fine.
- The keymap is completely trashed (dutch keyboard layout) so I can't login.
- Apparently, the J680 can "suspend" while running jLime.
- Boots Linux
- Runs X with IceWM
- Various X Apps work fine (MiniMO Browser, aterm, etc)
- Recognizes PCMCIA Ethernet and 802.11b/g wireless cards
- Can't seem to use the network, even when configured properly (dhcp doesn't get an address, wireless cards can't associate to open, unencrypted networks, etc)
- Cannot go into suspend mode properly. The backlight stays on, limiting battery life.
- After halting, the PDA can't reboot without a hard reset (removal of main and backup battery at the same time)
Labels: computing, handhelds, jornada, kansascity, linux, Operatingsystems, unix
2008-04-04
April Kansas City 2600 Meeting Sneak Preview

jlime Linux on the HP Jornada 720 Handheld/PC
This and a bunch of other stuff at the KC 2600 meeting.
Tonight (Friday, April 4 2008)
Oak Park Mall Food Court (Northeast entrance)
SE Corner of 95th and Quivira in Overland Park, KS
Starts at 5:00PM. Look for geeks with laptops.
Labels: InfoSec, kansascity, linux, meetings, unix
2008-04-02
UNIX Tip: Double Dashes
Files that start with a dash can cause problems if you don't know how to deal with them. Let's take a look:
Chimera:Documents axon$ ls -1The file "-file.doc" will cause problems with most command-line tools because they think -file.doc is an argument, not a file name.
-file.doc
2008-03-30.mp3
BitPIM.dmg
H-i-R.xcf
Parts.odt
vCards
Chimera:Documents axon$ cat -file.docSee what I mean?
cat: illegal option -- f
usage: cat [-benstuv] [file ...]
Chimera:Documents axon$ rm -file.doc
rm: illegal option -- l
usage: rm [-f | -i] [-dPRrvW] file ...
unlink file
Chimera:Documents axon$ mv -file.doc file.doc
mv: illegal option -- l
usage: mv [-f | -i | -n] [-v] source target
mv [-f | -i | -n] [-v] source ... directory
Placing two dashes anywhere in the argument list of almost every shell utility will tell that utility that all of the optional arguments have been passed and that anything following the double dash is to be taken literally -- usually this means it's a filename*. This lets you manipulate files that would otherwise cause you problems.
Chimera:Documents axon$ cat -- -file.docFor clarity, I used ls -1 (the number one not the lowercase letter "L" ) to force output to one filename per line.
this is a test file.
Chimera:Documents axon$ mv -- -file.doc file.doc
Chimera:Documents axon$ ls -1
2008-03-30.mp3
BitPIM.dmg
H-i-R.xcf
Parts.odt
file.doc
vCards
* For certain things, the literal arguments are passed on to a separate utility or script. A good example of this: Most startx scripts process command-line arguments, but you can use -- to pass additional arguments directly to the X Server, untouched by the startx script.




