The space is really coming together, and tonight looked like I expect many nights will look as we prepare to open the space 24/7 for makers, hackers, and tinkerers to collaborate with one another.
It was retro-computing night, apparently. This is my Zenith ZWL-184-97 "SuperSport". It's rocking an upgraded 8087 CPU at 8MHz, a 20MB built-in HDD and a 4-greyscale CGA monitor.

Victor tore into his Apple //e. He feared that the drive had been "eating" disks, so he took to it with Everclear. One drop for the read head. One shot for Victor. Two drops for read head. One, Two shots for Victor. No, he didn't drink it.


The ultimate test: Oregon Trail! Success!
Nekkid Apple pr0n:
Someone put a license plate frame on the plate I donated to the space.
And hevnsnt brought in the LED banner
... then Jestin defaced it...
Billy Crook's Remote-camera robot was a big hit. The camera mounted on the claw transmits audio and video back to the visor being held in the background.

A Robot's eye view:
Arduino hacking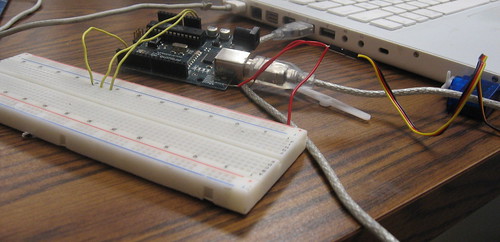
An old rack-mount modem bank, repurposed as an LED display project.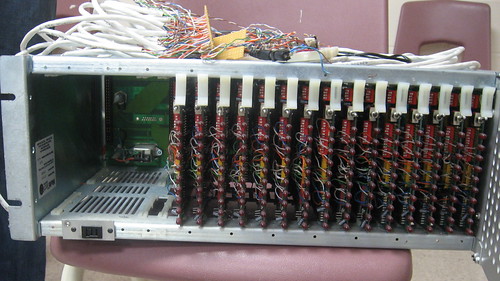
This robot is controlled by an R/C car remote and uses normal (albeit slightly modified) R/C servos. It's designed to fit inside a typical hamster ball and then you can stroll around. Sorry, no camera attached to this one.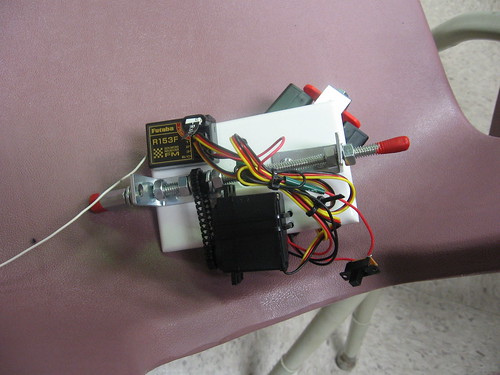
2009-02-26
CCCKC Photo Dump
Labels: ccckc, hackerspace, meetings
2009-02-24
Cowtown Computer Congress Grand Opening [Kansas City]
 The hour draws neigh. On March 2nd, Kansas City's hackerspace will be open for 24/7 access to members. To kick it off, there will be a week full of Grand Opening events. Check the CCCKC Wiki's Grand Opening page for an up-to-the-moment list of what's going on.
The hour draws neigh. On March 2nd, Kansas City's hackerspace will be open for 24/7 access to members. To kick it off, there will be a week full of Grand Opening events. Check the CCCKC Wiki's Grand Opening page for an up-to-the-moment list of what's going on.
Friday, March 6th would traditionally be the 2600 Meeting at Oak Park Mall, but several attendees will be at the CCCKC Opening instead. Further, all of the HiR folks from Kansas City will be giving presentations on interesting topics: Retro-Computing, Moodle: An Open-Source Education Suite, and Hacking La Fonera routers.
Depending on how much of the usual 2600 crew shows up, we may (or may not!) decide to switch the official meeting space to the Cave. After all, it's not far off the highway and it's close to Westport for plenty of post-meeting dining and drinking. Plus, it would be easier to communicate without all the distractions and noise of the mall.
If you're even remotely near Kansas City, it'd probably be worth your time to come out at least to see the talks Friday and maybe stick around for the DJ Bash on Saturday night.
Labels: ccckc, hackerspace, kansascity, meetings
2009-02-22
La Fonera Lab: Interesting Observartions
Asmodian X and I will be giving a talk on hacking the La Fonera and several other kinds of wireless routers at CCCKC's Opening Week festivities. Our talk will be Friday and that means that the usual 2600 meeting will be not at Oak Park Mall, but at the freshly opened hackerspace for March. KC 2600-goers, keep this in mind!
This evening, Asmo and I worked on a few things related to the Fon. One thing I tried: re-installing the OEM La Fonera firmware (0.7.1r1). I did this for a few reasons:
- To document unlocking ssh
- To document the process of enabling RedBoot
- To let it run its auto-upgrade (which everyone warns you against, it fixes the bug allowing you to enable ssh/redboot!)
- Maybe even document how to backgrade it to 0.7.1r1 (thus allowing you to unlock it even if it's got a newer version installed)
Without RedBoot, you must set up an elaborate network that emulates Fon's firmware server and hands an old version off as an "upgrade", tricking the router into installing the old version. It's not really that hard, but you need a web server, a router and DNS server running on an Internet-isolated lab network.
I also figured out that once you enable SSH, you can let it run its firmware upgrades to the latest version and SSH still starts. You can still have the best of both worlds: An official La Fonera hot-spot, with shell access to tinker around. I may see if I can get Jasager working while retaining La Fonera's latest firmware. That'll come later, though.
For those of you in the KC area, check out CCCKC's Grand Opening schedule. Hopefully we'll see you out there!
2009-02-11
Patch-O-Rama: Microsoft, Blackberry and AIX, Oh My!
First up, Microsoft issued four patches yesterday:
- MS09-002: IE (Critical)
- MS09-003: Exchange (Critical)
- MS09-004: SQL Server
- MS09-005: Visio/MS Office
Also, there's a new Blackberry bug in town.
Tip of the hat to Kevin's Infosec Ramblings for some of these.
Labels: AIX, blackberry, IBM, InfoSec, microsoft, patch, RIM, vulnerability, Windows
2009-02-10
Mac OS X Geek-Out: Text-mode boot
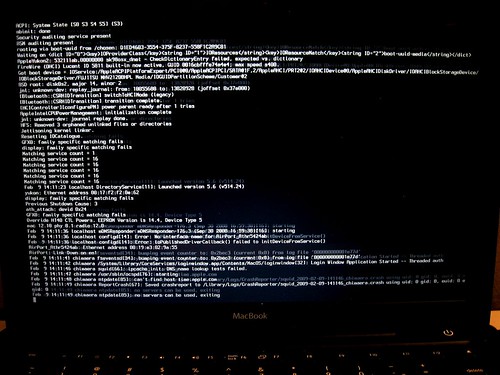
I know plenty of us come from a command-line background and like to see what's happening during the boot-up. By simply running this command inside Terminal on OS X, you get to see the boot messages (appropriately called "verbose mode") instead of a dull, blue screen while your Mac starts up.
sudo nvram boot=args="-v"
There are actually a few other interesting things you can do with the nvram command, but among them are some things that can cause your Mac to not boot. I do know that if you boot with the -s argument, it will go into single-user mode without getting prompted for the root password, but that's typical BSD stuff.
2009-02-09
Hacking Sleep (or why a 'bedtime' is over-rated)
 HiR's response? "Go to bed earlier!"
HiR's response? "Go to bed earlier!"
2009-02-05
Fun with Google Sketchup: CCCKC Floorplans
Pretty much from the get-go, I've been ready to help as needed with CCCKC's build-out and design team. On Tuesday, we took a tour of the new space to get a feel for how we'd try to set it up. I went to work creating what I saw in my mind's eye, using Google Sketchup. At this evening's meeting, I went ahead and presented it to the attendees. I got a lot of good input from everyone, and came away with a few really good ideas. There's a lot of work to be done.
Here's a photo from the loading dock entrance (all the parking we can use is above ground, but I walked in through the cave entry this evening)
Here's what I came up with in Sketchup. There are tons of free 3D Models for furniture and appliances. I love it. The space is about 1,400 square feet, and the space is almost a perfect square, divided into four rooms. I was just guessing when I drew the walls into place on Tuesday night, but tonight I confirmed that my guesses were close enough.
The main room will be the primary meeting place for affiliate organizations. I see this room needing a lot of flexibility. This is kind of what the space could look like when you enter. The green wall shown above probably won't work exactly like that. We'll probably try to get a pull-down green screen and a projector screen and mount it near the front of the room.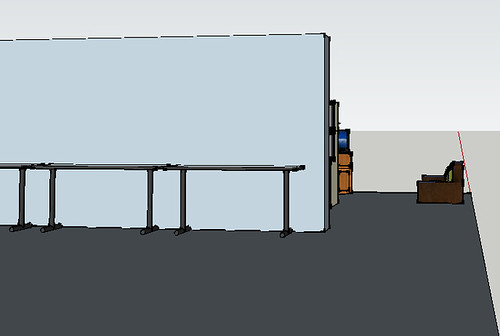
Easily-moved tables and nesting or folding chairs will be a major bonus here. It can be wide-open for social events, the tables forming an island for user-group meetings, or arranged into classroom-like rows for seminars, for example. From the front of the meeting room, it could look something like this.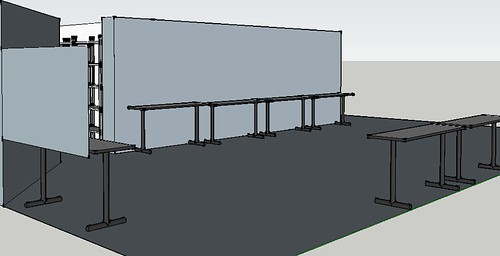
The room near the front of the meeting room will be telecom, material storage, and the home of the CCCKC Library: a shared pool of books, manuals, movies, and other media. There will be a full-height telecom rack (not enclosed) and probably a half-height server cage, even though I used a full-size model in this rendering.
The middle room will be the workshop. There will be at least one full-size workbench and a table. This will likely be filled out with things like a band saw, drill press and soldering stations. We might even see about fitting a drafting table in here.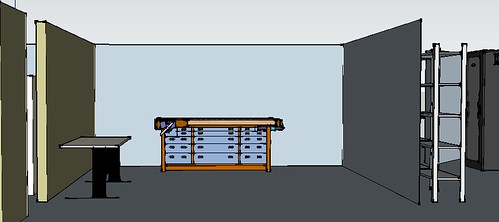
I am envisioning the "kitchen" area being a social hub with at least one sofa, a TV, and definitely some game consoles. It'll be a good place to chill after working on something in the workshop, and maybe a good place to take a nap if you find yourself staying in the hacker cave until the wee hours of the morning working on stuff.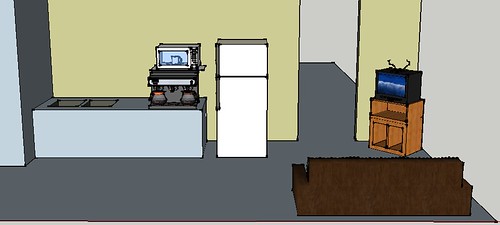
Right now, though, it's just four rooms with some old office furniture.
That brings us to a few important points:
There are some things we already have or that members are already donating: The 2-pot coffee maker, TV, consoles, shelving, the server/telecom racks, fridge and a few old crappy desks.
Things we really need. If you have any of these in Kansas City and feel like donating, we could use this stuff:
- Classroom tables
- Folding or nesting chairs
- Sofa
- Workbench
- Pull-down Green Screen / Projector screen
- Projector
- Also, for the love of all things good, pick up a MacBook raffle ticket - It'll help cover rent and operating expenses for the future. Raffle closes March 1!
Labels: ccckc, hackerspace, kansascity
2009-02-02
Embedded Linux appliance project
I put together an article on making embedded network appliances a while back ago. It was a little bit on the abstract side.
Now, I find myself helping out on a collaborative project with Cowtown Computer Congress and the KC Robotics Society. The Wii Labyrinth was a big hit, and now they've got a chance to build a giant 10' x 12' version for Science City. You can read more on Vince's blog.
One of the concerns is getting a reliable computer "brain" that can pull the parts of this project together. Some requirements:
- Runs Linux
- Can run the dependencies for the project (easy to compile for)
- Has USB (for the bluetooth and Arduino)
- Can be powered on and off by Science City staff without a shutdown procedure i.e. flipping a wall switch.
I opted to help the project out by building a Linux Appliance out of old x86 hardware. This means I can run a more feature-rich environment, but build it like an appliance. I proposed the following to meet the requirements of easy power-up and power-down:
- Logical partitions are mounted read-only or unpacked to ramdisk and dismounted
- Dynamic data is loaded to ramdisk if needed (i.e. /tmp)
- BIOS settings are tuned to skip as many POST checks as possible (don't halt on keyboard/video errors, skip RAM check, don't scan for new IDE devices, etc)
Rubber-hose cryptanalysis and how to not get a wrench to the head
From xkcd this morning:
In the security industry, we call this "rubber-hose cryptanalysis" -- a euphemism coined by Marcus Ranum for getting the target to give you access to the encrypted data via coercion. The name implies physical torture, but psychological coercion (threatening physical harm, litigation, etc) is pretty much the same thing. I personally consider this a variety of Social Engineering since it relies on manipulating your mark rather than using technology to directly attack the assets.
When attacking many modern cryptosystems, a technological attack is often going to take a lot longer than simply bludgeoning it out of someone. Some technological attacks that don't directly involve breaking the crypto through brute force can sometimes get decrypted data :
- Dumping the contents of the target's RAM and Swap file (can contain the crypto key, unencrypted data, evidence of encrypted data or metadata about the encrypted files)
- Operating system history "recently used" (can store history data and reveal structure of the encrypted volume)
Simply put, deniable encryption most often refers to encrypted data which can resolve to both the genuine data and decoy data, depending on the key used to decrypt the data. The decoy data should appear to be "secret" in nature, and it's best if the decoy data appears to be the same kind of data that you're really trying to protect. If you encrypted a bunch of proprietary documentation, your attacker may know what they're looking for. You'd be best to make the decoy data look like proprietary documentation while remaining innocuous, perhaps loaded with misleading facts. Using a video of Rick Astley's Never Gonna Give You Up might tip the attacker off that they need to keep looking (and torturing you) for the real goods.
While not the only tool available, one commodity piece of free, cross-platform software that handles this task quite nicely is TrueCrypt. It handles full-disk encryption, deniable encryption (which is called a "hidden volume" in TrueCrypt), and can even boot an operating system from a hidden volume. That's right, TrueCrypt can boot an entirely different operating environment based on which pre-boot passphrase you enter.
I'll save the merits and woes of full-disk encryption for another day.
Labels: encryption, humor, InfoSec, socialengineering, software, tools




