2010-02-26
Risk Assessment: Electronic Lock Impressioner
Labels: lockpicking, locks, physicalsecurity, risk
2010-02-22
Teaching curiosity
A theme that commonly comes up among security professionals and hackers:
- Logic and Critical Thinking
- Research Skills
- Technical writing
- Public Speaking
- Elementary Debate
- Any introductory course that provide hands-on lab time to learn the Scientific Method
Labels: education
2010-02-21
2010-02-14
Fraud and Identity Theft are not "Hacking"
[H]ard|OCP: Hacker gets record 13-year sentence for hacking.
Labels: computer hacker, hackers, news, rant
2010-02-11
Oh noes! Google Buzz FUD!
Silicon Valley Insider came up with this wonderful sensationalist FUD piece: WARNING: Google Buzz has a huge privacy flaw!



2010-02-09
IT Security Certifications: Path to payday, or just a farce?
Labels: career, certifications, InfoSec
Juxtaposition - Subscription-walls
A new paper on Johnny's "I Hack Stuff" blog requires a subscription. Meanwhile, Sensepost is abandoning their "Regwall" for research papers.
2010-02-08
Wrapping insecure web apps with Apache
When dealing with a web service which for one reason or another cannot or should not be allowed on the web. Apache has several wonderful modules which allows the services to be wrapped and behave like a web app should (working SSL certificates, forced encryption, authentication ...)
In this article I will discuss and show some examples on how to create an authenticated reverse proxy with mod_authnz, mod_proxy,mod_rewrite and mod_security.
-=-=-=-=-=-=-=-ToC-=-=-=-=-=-=-=-
1. Prerequisites
2. Installation of Apache
3. Configuration of Apache
4. Configuration of mod_rewrite
5. Configuration of mod_proxy
6. Configuration of mod_authnz(optional)
7. Configuration of mod_security
8. Summary
9. Informative Resources
-=-=-=-=-=-=-=--=-=-=-=-=-=-=-=-=-
1. Prerequisites
In this example you will need:
- Ubuntu Linux
- LDAP compatible server with valid SSL certificate
- Apache2
- Wildcard ssl certificate or valid certificates for each service published
- Apache mod_rewrite
- Apache mod_proxy
- Apache mod_authnz
- Apache mod_security
Install Apache2 by any of your favorite package managers or at the prompt:
sudo apt-get install apache23. Configuration of Apache
Then create a new config file for each of your new relays.
Inside of the virtual host tag:
UseCanonicalName Off4. Configuration of mod_rewrite
LogFormat "%V %h %l %u %t \"%r\" %s %b" vcommon
#incase you have a self signed certificate on the ldap server
LDAPVerifyServerCert offSSLEngine On
SSLCertificateFile /etc/apache2/ssl/generic/example.com.crt
SSLCertificateKeyFile /etc/apache2/ssl/generic/example.com.key
Servername weirdone_wrapped.example.com
CustomLog /var/log/apache2/access_log.relay-weird.vhost vcommon
(mod-rewrite is included with apache2)
To enable mod_rewrite:
a2enmod rewriteThen add the following virtual host entry to redirect http traffic:
5. Configuration of mod_proxyRewriteEngine On
#Force HTTPS
RewriteCond %{HTTPS} !=on
RewriteRule ^(.*) https://%{SERVER_NAME}/$1 [R,L]
First install additional mod_proxy:
sudo apt-get install libapache2-mod-proxy-htmlThen enable the modules:
a2enmod proxy proxy_connect proxy_html proxy_httpInsert the proxy section and commands into the SSL (port 443) vhost section:
6. Configuration of mod_authnz(optional)Order deny,allow ProxyPreserveHost On ProxyPass / http://weirdapp.example.com:50281/ ProxyPassReverse / http://weirdapp.example.com:50281/
First install mod_authnz:
apt-get install libapache2-mod-authnz-externalThen insert the following into the proxy block for ldap authentication of the connection:
AuthType Basic AuthBasicProvider ldap
AuthName "Please authenticate your connection using your network login."
#Some Ldap servers will reject un-encrypted simple authentication, plus this is
#just a good idea any way.
AuthLDAPURL "ldaps://1.2.3.4/?cn" SSL
AuthzLDAPAuthoritative on
AuthLDAPBindDN cn=authbot,ou=users,o=org
AuthLDAPBindPassword password
AuthLDAPRemoteUserAttribute uid
AuthLDAPRemoteUserIsDN on
AuthLDAPGroupAttributeIsDN on
AuthLDAPGroupAttribute member
Require ldap-group cn=Staff,ou=groups,o=org
Satisfy All
7. Configuration of mod_security
First install mod_security:
apt-get install libapache-mod-securityThen enable it:
a2enmod mod-securityMod_security is fairly tricky, I am using a default configuration but I am only logging errors and not preventing them. Configuration beyond this is outside the scope of this article.
Edit /etc/apache2/mods-available/mod_security.conf and use the configuration example in
"/usr/share/doc/mod-security-common/examples/" as a template.
If it proves to be too restrictive, you can switch the part which says:
SecRuleEngine On
to
SecRuleEngine DetectionOnly
8. Summary
So, after this is installed, Apache will listen to a static IP then relay a a website to the end user over SSL after authenticating the connection with an LDAP server. And if anything fishy happens it will be logged/(or blocked) with mod-security.
This is not a 100% silver bullet solution. Apache http authentication is generally a bad idea, especially over an unencrypted session. In this example it is partially mitigated with mod_rewrite but at this time Apache does not natively support any modern authentication technologies with hooks for LDAP or any other authentication service. If you have the opportunity to prevent the need to do this then make it so.
The best way is to do it right the first time and write into your web application (or specify in the RFQ) the correct security measures.
9. Informative Resources
Breach Security "Mod Security home page". (Accessed April 2009)
http://www.modsecurity.org
The Apache Software foundation. "Apache webserver website". (accessed Jan 2010)
http://httpd.apache.org/
See also :
Asmodian X's Securing php web applications:
http://www.h-i-r.net/2009/05/securing-php-web-applications.html
Ax0n's OAMP (Apache, Mysql, PHP on OpenBSD) Article:
http://www.h-i-r.net/2008/12/sysadmin-sunday-amp-on-openbsd-44.html
Asmodian X's Name based hosting mini-howto:
http://www.h-i-r.net/2008/10/sysadmin-sunday-apache-name-based.html
Asmodian X's Workbench - Suhosin :
http://www.h-i-r.net/2008/12/asmodians-workbench-suhosin-hardened.html
2010-02-06
Guest post: Fonera Power-Over-Ethernet
Editor's notes:
This technique should be useful for short runs of ethernet (6' or less) and to power pretty much anything that needs 5VDC and doesn't require a lot of current. I've seen USB ports provide up to one amp of current, though it's usually advised to keep it under 500mW. If you have a dual-USB Power/Data cord like the ones that come with external 2.5" hard drives, I'd advise using that to help get more power to the Fon, but there are several people running USB power directly to the Fon, and it seems to work fine. This is the first time I've seen a POE injector/splitter used in combination with USB before. Pretty clever.
This is a guest post by cyb3rassasin, a student in the midwest that's interested in security technologies. You can follow him on Twitter. 
Okay, so I’m sitting in the coffee shop with my LaFonera router in front of me, and my netbook on my lap. I look at my fon just sitting there with its 4 AA battery pack, pondering how else I could power this little guy. A battery pack is bulky, and I don’t really want to have to carry a wall wart with me everywhere I go.
So the options that come to mind are usb power, battery pack, and power over ethernet. The first two aren’t bad ideas but I was kinda looking for something a little more compact and cleaner. I decided to look at some PoE injectors/splitters because they’re inexpensive and compact.
The only problem I could forsee is again I’d have to carry a wall wart around with me. Then I thought why not cut the power adapter off the injector and replace it with a usb plug. It would be simple, clean, and I’d only have to have one cable running to the fon. The Fon can run from 5VDC just fine.
I decided to pick up a set of PoE cables from Passive PoE. I grabbed a usb cable from an old phone that I had, I chopped the end off and stripped all the wires. I then cut the power plug off of the injector and stripped the two wires. ( note: the copper is ground and the red is positive)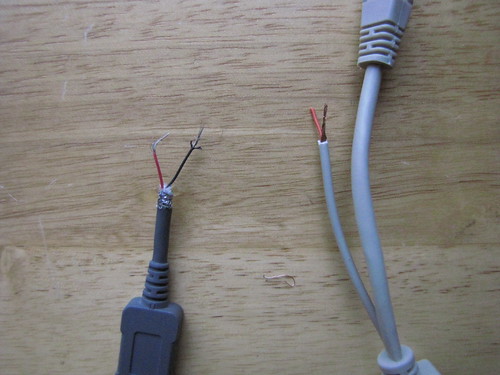
Now, don’t make the same mistake I did: put the heatshrink on the injector before soldering the usb plug and the injector together. I soldered up the connections, wrapped each individual connection in electrical tape, and heatshrunk it.

Before testing this with my fon, I thought it would be a good idea to make sure I got the polarity correct. I plugged the injector into my netbook, hooked up an ethernet cable, and then attached the splitter. I took a multi-meter and to the splitter and sure enough, I had the polarity right. Center pin: positive 5VDC, outer barrel: negative
Now it’s time to take a leap of faith and plug in my fon, and woot! It works!
So now I successfully have a compact way to power my fon via usb and PoE. I’ve found one downside to this, it drains my netbook battery faster than if I would use a battery pack. Other than that this is an effective alternative way to power the fon.
cyb3rassasin also showed me the Open-Mesh mini router, which seems to be nearly identical to the original Fon2100 shown here. Since the Fon2100 is no longer available new from the manufacturer, and the newer hardware isn't as friendly for things like Jasager/Karma, it's nice to know there is still a comparable piece of gear out there to take its place in our hackpacks. Long live evil wifi! Here are some photos he sent us, comparing the Open-Mesh and the Fon2100.


Labels: Electronics, fon, guestposts, hacks, poe, wireless









