I like to tunnel SSH, whether it's for getting around a captive portal at an airport or for encrypting your traffic at DefCon.
At home, I use an old NetScreen1 5XP-Elite firewall. The "Elite" has absolutely nothing to do with its mad $k1llz. It just means it's got an unlimited network license, which is good because I have a lot of freaking computers in the Lab-O-Ratory.
I wanted to run SSH over port 53 (DNS) as well as 22 to aid in tunneling SSH where external DNS is allowed (more often than you'd think) but I got this error via the GUI:
On the CLI, I was met with this:
ns5-> set vip untrust-ip 53 SSH 192.168.0.56Well... CRAP!
###Invalid reserved vip port number 53 for SSH service!
I don't usually take "no" for an answer too easily. Some javascript told me I couldn't do it. Some little parameter within the CLI told me the same thing. I have a pretty hard time believing that the kernel of my firewall is incapable of spawning an SSH forward on port 53 when port 22 or 31337 would work just fine. Skepticism of limitations is one of the fundamental elements of having the security mindset.
I poked through the web-page source code that renders the page, but it's all on-the-fly javascript. I decided that if I wanted to see what the form post was passing, it would be easier to sniff the session. I went ahead and fired up my old friend, Wireshark.2
Notice that the web admin interface is only running on the internal interface, so I'm tunneling port 80 direct to it through one of my systems on the inside, hence the localhost:80 http session. I opted to redirect port 2201 to the internal SSH box, since it's well within the range of acceptable ports. I did a "Follow TCP Stream" and VOILA!
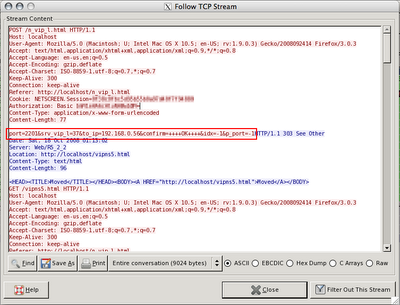
This gives me everything I need to make a quick HTML file that posts whatever port number I want as the "port" variable. I decided to take the easy way out and see if NetScreen's web interface would accept the variables as a GET, by pasting it into the location bar instead, just to see. I broke it up into three lines here, but you can see the only thing I changed was "2201" to "53".
http://localhost/n_vip_l.html?
port=53&srv_vip_l=37&to_ip=192.168.0.56&
confirm=++++OK++++&idx=-1&p_port=-1
Success!

What's the point? This was a practical example for how to putz around with stuff you may already have and dabble in the fascinating world of web application security. As mentioned before, it's also an exercise in thinking beyond limitations.
NetScreen was founded by a bunch of ex-Cisco guys and the IOS-esque "ScreenOS" as it's called really shows it. In 2004, NetScreen was snarfed up by Juniper Networks. Juniper's low-end SSG-5 is about the closest living relative to my beloved yet crufty home firewall.
On an odd side-note, Frogman and I got to see Gerald Combs (creator of the project now called Wireshark) give one of his very, very rare talks on TCP/IP, which included a lot of Ethereal's backstory.


